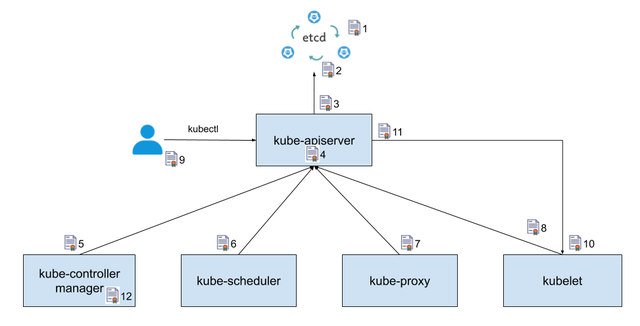
Kubernetes 中使用了大量的证书,本文不会试图覆盖到所有可能使用到的证书,但会讨论到主要的证书。理解了这些证书的使用方法和原理后,也能很快理解其他可能遇到的证书文件。下图标识出了在 kubernetes 中主要使用到的证书和其使用的位置:
二进制各个证书默认过期时间
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
/etc/kubernetes/ssl/ca.pem #10年有效期(根证书) /etc/kubernetes/ssl/apiserver.pem #1年有效期 /etc/kubernetes/ssl/k8s-apiserver-admin.pem #1年有效期(客户端证书) /etc/kubernetes/ssl/aggregator.pem #1年有效期[webhook 证书] /etc/kubernetes/ssl/etcd/ca.pem #10年有效期(etcd根证书) /etc/kubernetes/ssl/etcd/server.pem #1年有效期(etcd服务证书) /etc/kubernetes/ssl/etcd/etcd-member-k8s-master-1#1年有效期(etcd节点证书) /etc/kubernetes/ssl/apiserver-etcd-client.pem #1年有效期(etcd客户端证书) /etc/kubernetes/ssl/etcd/peer.pem #1年有效期(peer通信证书) /etc/kubernetes/ssl/kubelet-client.pem #1年有效期(客户端证书) /etc/kubernetes/ssl/k8s-controller-manager.pem #1年有效期(客户端证书) /etc/kubernetes/ssl/k8s-scheduler.pem #1年有效期(客户端证书) /etc/kubernetes/ssl/k8s/kube-proxy.pem #1年有效期(客户端证书) |
|
1 2 |
注意:与api交互的组件,配置文件一般不需指定证书(例:kubectl,kubelet,kube-proxy)。 如果组件要监听ssl端口,配置文件就需要指定证书 |
查看确认证书到期时间
|
1 2 3 4 5 |
openssl x509 -noout -text -in /etc/kubernetes/ssl/ca.pem | grep Not openssl x509 -noout -text -in /etc/harbor/cert/server.crt | grep Not openssl x509 -noout -text -in m | grep Not |
一、更新CA根证书和秘钥 (一般有效期10年基本不用动)
|
1 2 |
CA (Certificate Authority) 是自签名的根证书,用来签名后续创建的其它证书。 CA 证书是集群所有节点共享的,只需要创建一次,后续用它签名其它所有证书(除了etcd) |
全局 配置文件生成(后续各个组件生成证书会用到)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
cat > /root/ca-config.json <<EOF { "signing": { "default": { "expiry": "876000h" }, "profiles": { "kubernetes": { "usages": [ "signing", "key encipherment", "server auth", "client auth" ], "expiry": "876000h" } } } } EOF |
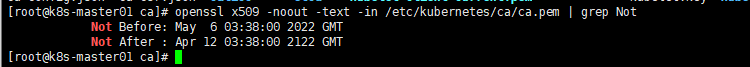
1. 确认证书到期时间
|
1 |
openssl x509 -noout -text -in /etc/kubernetes/ssl/ca.pem | grep Not |
2.新建ca证书签名请求文件ca-csr.json
|
1 2 3 |
#创建新目录来存放新证书,替换证书前先备份旧的配置 mkdir -p /root/ssl/k8s cd /root/ssl/k8s |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
cat > /root/ssl/k8s/k8s-ca-csr.json <<EOF { "CN": "kubernetes", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "Shooter" } ], "ca": { "expiry": "87600h" } } |
|
1 |
#可修改expiry为876000h 100年有效期 默认10年有效期貌似 |
2. 重新生成 CA 证书和私钥
|
1 2 3 4 |
cfssl gencert -initca /root/ssl/k8s/k8s-ca-csr.json | \ cfssljson -bare /root/ssl/k8s/k8s-ca ls -la /root/ssl/k8s/*-ca* |
查看证书有效期
3. k8s ca 新证书分发替换
|
1 2 3 4 5 6 |
# K8S 集群ca 证书 scp -r /root/ssl/k8s/k8s-ca* root@192.168.0.12:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s/k8s-ca* root@192.168.0.13:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s/k8s-ca* root@192.168.0.14:/apps/k8s/ssl/k8s #根据自己证书存放位置修改路径 |
二、 更新admin 证书和私钥(kubectl使用)
管理员用户通过 kubectl 访问 kube-apiserver 使用的证书,该证书是客户端证书。
说明:
|
1 2 3 |
kubectl 使用 https 协议与 kube-apiserver 进行安全通信,kube-apiserver 对 kubectl 请求包含的证书进行认证和授权。kubectl用到了admin证书 kubectl 后续用于集群管理,所以这里创建具有最高权限的 admin 证书。 |
1、 创建admin证书签名请求文件(或者用原来的也可):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
cat > /root/ssl/k8s/k8s-apiserver-admin.json << EOF { "CN": "admin", "hosts": [""], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "system:masters", "OU": "Kubernetes-manual" } ] } EOF |
|
1 2 3 |
O: system:masters:kube-apiserver 收到使用该证书的客户端请求后,为请求添加组(Group)认证标识 system:masters; 预定义的 ClusterRoleBinding cluster-admin 将 Group system:masters 与 Role cluster-admin 绑定,该 Role 授予操作集群所需的最高权限; 该证书只会被 kubectl 当做 client 证书使用,所以 hosts 字段为空 |
2、 重新生成admin证书与私钥
|
1 2 3 4 5 6 7 8 9 |
cfssl gencert \ -ca=/root/ssl/k8s/k8s-ca.pem \ -ca-key=/root/ssl/k8s/k8s-ca-key.pem \ -config=/root/ca-config.json \ -profile=kubernetes \ /root/ssl/k8s/k8s-apiserver-admin.json | \ cfssljson -bare /root/ssl/k8s/k8s-apiserver-admin ls -al /opt/k8s/cfssl/pki/k8s/k8s-apiserver-* |
3. 创建新的admin.kubeconfig文件
|
1 2 3 |
重要:kubectl 使用 kubeconfig 文件访问 apiserver,该文件包含 kube-apiserver 的地址和认证信息(CA 证书和客户端证书);kubectl是访问api所以配置文件不需要指定证书。 所以后面只需要分发配置文件其他节点不需要分发admin证书和私钥 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
mkdir -p /root/ssl/k8s/kubeconfig cd /root/ssl/k8s/kubeconfig kubectl config set-cluster kubernetes \ --certificate-authority=/root/ssl/k8s/k8s-ca.pem \ --embed-certs=true \ --server=https://192.168.0.12:5443 \ --kubeconfig=/root/ssl/k8s/kubeconfig/admin.kubeconfig # 设置客户端认证参数 kubectl config set-credentials admin \ --client-certificate=/root/ssl/k8s/k8s-apiserver-admin.pem \ --client-key=/root/ssl/k8s/k8s-apiserver-admin-key.pem \ --embed-certs=true \ --kubeconfig=/root/ssl/k8s/kubeconfig/admin.kubeconfig # 设置上下文参数 kubectl config set-context kubernetes \ --cluster=kubernetes \ --user=admin \ --namespace=kube-system \ --kubeconfig=/root/ssl/k8s/kubeconfig/admin.kubeconfig # 设置默认上下文 kubectl config use-context kubernetes --kubeconfig=/root/ssl/k8s/kubeconfig/admin.kubeconfig |
|
1 |
kubectl的kubeconfig文件里面保存着集群的apisever地址和你链接集群的身份验证 |
|
1 2 3 4 |
–certificate-authority:验证 kube-apiserver 证书的根证书; –client-certificate、–client-key:刚生成的 admin 证书和私钥,与 kube-apiserver https 通信时使用; –embed-certs=true:将 ca.pem 和 admin.pem 证书内容嵌入到生成的 kubectl.kubeconfig 文件中(否则,写入的是证书文件路径,后续拷贝 kubeconfig 到其它机器时,还需要单独拷贝证书文件,不方便。); –server:指定 kube-apiserver 的地址,这里指向第一个节点上的服务; |
4、分发新配置文件覆盖到其他节点(2选1)
|
1 2 3 4 5 6 7 8 9 10 11 |
1.分发config(所有使用kubectl的节点发放)[推荐] scp -r /root/ssl/k8s/kubeconfig/admin.kubeconfig root@192.168.0.12:~/.kube/config scp -r /root/ssl/k8s/kubeconfig/admin.kubeconfig root@192.168.0.13:~/.kube/config scp -r /root/ssl/k8s/kubeconfig/admin.kubeconfig root@192.168.0.14:~/.kube/config 2.使用环境变量(这种就不必复制成config了) scp -r /root/ssl/k8s/kubeconfig/admin.kubeconfig root@192.168.0.12:/opt/k8s/kubeconfig/admin.kubeconfig scp -r /root/ssl/k8s/kubeconfig/admin.kubeconfig root@192.168.0.13:/opt/k8s/kubeconfig/admin.kubeconfig scp -r /root/ssl/k8s/kubeconfig/admin.kubeconfig root@192.168.0.14:/opt/k8s/kubeconfig/admin.kubeconfig export KUBECONFIG=/opt/k8s/kubeconfig/admin.kubeconfig |
三、 更新api-server证书与私钥
kube-apiserver 对外提供服务使用的证书。该证书是服务器证书。
1、 生成新的 Kubernetes API Server 证书和私钥
|
1 2 3 4 5 6 7 8 9 |
cfssl gencert \ -ca=/root/ssl/k8s/k8s-ca.pem \ -ca-key=/root/ssl/k8s/k8s-ca-key.pem \ -config=/root/ca-config.json \ -profile=kubernetes \ /opt/k8s/cfssl/k8s/k8s-apiserver.json | \ cfssljson -bare /root/ssl/k8s/k8s-server #k8s-apiserver.json 使用集群原有的即可,此处不做新建 |
2、分发新证书到各个节点
|
1 2 3 4 |
# 分发apiserver 证书 scp -r /root/ssl/k8s/k8s-server* root@192.168.0.12:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s/k8s-server* root@192.168.0.13:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s/k8s-server* root@192.168.0.14:/apps/k8s/ssl/k8s |
四、 更新kube-controller-manager证书与私钥
kube-controller-manager 作为客户端访问 kube-apiserver 使用的证书,该证书是客户端证书。
1、创建 controller-manager 证书请求文件
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
cat > /root/ssl/k8s/k8s-controller-manager.json << EOF { "CN": "system:kube-controller-manager", "hosts": [""], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "$CERT_ST", "L": "$CERT_L", "O": "system:kube-controller-manager", "OU": "Kubernetes-manual" } ] } EOF |
2、 重新生成controller-manager证书与私钥
|
1 2 3 4 5 6 7 8 9 |
cfssl gencert \ -ca=/root/ssl/k8s/k8s-ca.pem \ -ca-key=/root/ssl/k8s/k8s-ca-key.pem \ -config=/root/ca-config.json \ -profile=kubernetes \ /root/ssl/k8s/k8s-controller-manager.json | \ cfssljson -bare /root/ssl/k8s/k8s-controller-manager ll /root/ssl/k8s/k8s-controller-manager* |
将生成的证书和私钥分发到所有 master 节点:
|
1 2 3 |
scp -r /root/ssl/k8s/k8s-controller-manager* root@192.168.0.12:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s//k8s-controller-manager* root@192.168.0.13:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s//k8s-controller-manager* root@192.168.0.14:/apps/k8s/ssl/k8s |
3、 创建 kube-controller-manager.kubeconfig
|
1 |
kube-controller-manager 使用 kubeconfig 文件访问 apiserver,该文件提供了 apiserver 地址、嵌入的 CA 证书和 kube-controller-manager 证书等信息: |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
kubectl config set-cluster kubernetes \ --certificate-authority=/root/ssl/k8s/k8s-ca.pem \ --embed-certs=true \ --server=https://127.0.0.1:6443 \ --kubeconfig=kube-controller-manager.kubeconfig kubectl config set-credentials system:kube-controller-manager \ --client-certificate=/root/ssl/k8s/k8s-controller-manager.pem \ --embed-certs=true \ --client-key=/root/ssl/k8s/k8s-controller-manager-key.pem \ --kubeconfig=kube-controller-manager.kubeconfig kubectl config set-context kubernetes \ --cluster=kubernetes \ --user=system:kube-controller-manager \ --kubeconfig=kube-controller-manager.kubeconfig kubectl config use-context kubernetes --kubeconfig=kube-controller-manager.kubeconfig |
4、 分发 kubeconfig 到所有 master 节点:
|
1 2 3 4 |
cd /root/ssl/k8s/ scp kube-controller-manager.kubeconfig root@192.168.0.12:/apps/k8s/config/ scp kube-controller-manager.kubeconfig root@192.168.0.13:/apps/k8s/config/ scp kube-controller-manager.kubeconfig root@192.168.0.14:/apps/k8s/config/ |
五、 更新kube-scheduler 证书与私钥
kube-scheduler 作为客户端访问 kube-apiserver 使用的证书,该证书是客户端证书。
1、创建证书签名请求:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
cat > /root/ssl/k8s/k8s-scheduler.json <<EOF { "CN": "system:kube-scheduler", "hosts": [""], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "system:kube-scheduler", "OU": "Kubernetes-manual" } ] } EOF |
|
1 2 3 |
hosts 列表包含所有 kube-scheduler 节点 IP; CN 和 O 均为 system:kube-scheduler,kubernetes 内置的 ClusterRoleBindings system:kube-scheduler 将赋予 kube-scheduler 工作所需的权限; 生成证书和私钥: |
2、生成新证书和私钥
|
1 2 3 4 5 6 7 8 9 |
cfssl gencert \ -ca=/root/ssl/k8s/k8s-ca.pem \ -ca-key=/root/ssl/k8s/k8s-ca-key.pem \ -config=/root/ca-config.json \ -profile=kubernetes \ /root/ssl/k8s/k8s-scheduler.json | \ cfssljson -bare /root/ssl/k8s/k8s-scheduler ls -al /root/ssl/k8s/k8s-scheduler* |
3、 将生成的证书和私钥分发到所有 master 节点
|
1 2 3 |
scp -r /root/ssl/k8s/k8s-scheduler* root@192.168.0.12:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s/k8s-scheduler* root@192.168.0.13:/apps/k8s/ssl/k8s scp -r /root/ssl/k8s/k8s-scheduler* root@192.168.0.14:/apps/k8s/ssl/k8s |
4、创建k8s-scheduler.kubeconfig
|
1 |
kube-scheduler 使用 kubeconfig 文件访问 apiserver,该文件提供了 apiserver 地址、嵌入的 CA 证书和 kube-scheduler 证书: |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
cd /root/ssl/k8s/ # 设置集群参数 kubectl config set-cluster kubernetes \ --certificate-authority=/root/ssl/k8s/k8s-ca.pem \ --embed-certs=true \ --server=https://127.0.0.1:6443 \ --kubeconfig=kube-scheduler.kubeconfig # 设置客户端认证参数 kubectl config set-credentials system:kube-scheduler \ --client-certificate=/root/ssl/k8s/k8s-scheduler.pem \ --embed-certs=true \ --client-key=/root/ssl/k8s/k8s-scheduler-key.pem \ --kubeconfig=kube-scheduler.kubeconfig # 设置上下文参数 kubectl config set-context kubernetes \ --cluster=kubernetes \ --user=system:kube-scheduler \ --kubeconfig=kube-scheduler.kubeconfig # 设置默认上下文 kubectl config use-context kubernetes --kubeconfig=kube-scheduler.kubeconfig |
分发 kubeconfig 到所有 master 节点:
|
1 2 3 4 |
cd /root/ssl/k8s/ scp kube-scheduler.kubeconfig root@192.168.0.12:/apps/k8s/config/ scp kube-scheduler.kubeconfig root@192.168.0.13:/apps/k8s/config/ scp kube-scheduler.kubeconfig root@192.168.0.14:/apps/k8s/config/ |
六、更新 kube-proxy 证书与私钥
kube-proxy 作为客户端访问 kube-apiserver 使用的证书,该证书是客户端证书。
1、 创建证书签名请求:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
cat > /root/ssl/k8s/kube-proxy.json << EOF { "CN": "system:kube-proxy", "hosts": [""], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "system:node-proxier", "OU": "Kubernetes-manual" } ] } EOF |
2、 生成 kube-proxy 新证书和私钥:
|
1 2 3 4 5 6 7 8 9 |
cfssl gencert \ -ca=/root/ssl/k8s/k8s-ca.pem \ -ca-key=/root/ssl/k8s/k8s-ca-key.pem \ -config=/root/ca-config.json \ -profile=kubernetes \ /root/ssl/k8s/kube-proxy.json | \ cfssljson -bare /root/ssl/k8s/kube-proxy ls -al /opt/k8s/cfssl/pki/k8s/kube-proxy* |
|
1 |
kube-proxy是访问api所以不需要指定证书。不需要分发证书和私钥 |
3、 创建kube-proxy.kubeconfig文件
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
cd /root/ssl/k8s/ kubectl config set-cluster kubernetes \ --certificate-authority=/root/ssl/k8s/k8s-ca.pem \ --embed-certs=true \ --server=https://127.0.0.1:6443 \ --kubeconfig=kube-proxy.kubeconfig kubectl config set-credentials system:kube-proxy \ --client-certificate=/root/ssl/k8s/kube-proxy.pem \ --client-key=/root/ssl/k8s/kube-proxy-key.pem \ --embed-certs=true \ --kubeconfig=kube-proxy.kubeconfig kubectl config set-context default \ --cluster=kubernetes \ --user=system:kube-proxy \ --kubeconfig=kube-proxy.kubeconfig kubectl config use-context default --kubeconfig=kube-proxy.kubeconfig |
4、分发 kubeconfig 文件:
|
1 2 3 4 5 |
cd /root/ssl/k8s/ scp kube-proxy.kubeconfig root@192.168.0.12:/apps/k8s/conf scp kube-proxy.kubeconfig root@192.168.0.13:/apps/k8s/conf scp kube-proxy.kubeconfig root@192.168.0.14:/apps/k8s/conf |
5、kubelet证书更新看这篇传送门。
6、etcd证书更新 传送门。
|
1 |
有参考 https://baijiahao.baidu.com/s?id=1709354401388871458&wfr=spider&for=pc |
- 本文固定链接: https://www.yoyoask.com/?p=8358
- 转载请注明: shooter 于 SHOOTER 发表