|
1 2 3 |
etcd 集群中各个节点之间相互通信使用的证书。由于一个 etcd 节点既为其他节点提供服务,又需要作为客户端访问其他节点,因此该证书同时用作服务器证书和客户端证书。 etcd 集群向外提供服务使用的证书。该证书是服务器证书。 kube-apiserver 作为客户端访问 etcd 使用的证书。该证书是客户端证书。 |
更新etcd证书
|
1 2 3 |
#创建新目录来存放新证书,替换证书前先备份旧的配置 mkdir -p /root/ssl/etcd cd /root/ssl/etcd |
1、创建etcd服务根证书
1.1创建etcd服务根证书签名请求文件
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
cat > /root/ssl/etcd/etcd-ca-csr.json <<EOF { "CN": "etcd", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "Shooter" } ], "ca": { "expiry": "876000h" } } EOF |
1.2. 生成新的 etcd CA 根证书
|
1 2 3 4 |
cfssl gencert -initca /root/ssl/etcd/etcd-ca-csr.json | \ cfssljson -bare /root/ssl/etcd/etcd-ca ls -la /root/ssl/etcd/*-ca* |
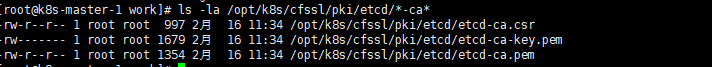
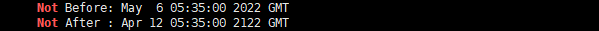
查看新证书有效期
|
1 |
openssl x509 -in xx.crt -noout -dates |
1.3. 分发etcd新生成的CA根服务证书文件
|
1 2 3 4 5 6 |
# etcd 集群ca 证书 scp -r /root/ssl/etcd/etcd-ca* root@192.168.0.12:/apps/etcd/ssl scp -r /root/ssl/etcd/etcd-ca* root@192.168.0.13:/apps/etcd/ssl scp -r /root/ssl/etcd/etcd-ca* root@192.168.0.14:/apps/etcd/ssl #根据自己证书存放位置修改路径 |
2、创建etcd服务证书
2.1、创建证书签名请求:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
cat > /root/ssl/etcd/etcd-server.json << EOF { "CN": "etcd", "hosts": [ "127.0.0.1", "192.168.0.12","192.168.0.13","192.168.0.14", "k8s-master-1","k8s-master-2","k8s-master-3" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "Shooter" } ] } EOF |
2.2、生成证书和私钥:
|
1 2 3 4 5 6 7 |
cfssl gencert \ -ca=/root/ssl/etcd/etcd-ca.pem \ -ca-key=/root/ssl/etcd/etcd-ca-key.pem \ -config=/root/ssl/etcd/ca-config.json \ -profile=kubernetes \ /root/ssl/etcd/etcd-server.json | \ cfssljson -bare /root/ssl/etcd/etcd-server |
3、创建etcd节点证书
|
1 |
etcd 集群中各个节点之间相互通信使用的证书。由于一个 etcd 节点既为其他节点提供服务,又需要作为客户端访问其他节点,因此该证书同时用作服务器证书和客户端证书。 |
3.1、创建证书签名请求文件(多个节点依次执行即可)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
cat > /root/ssl/etcd/k8s-master-1.json << EOF { "CN": "etcd", "hosts": [ "127.0.0.1", "192.168.0.12", "k8s-master-1" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "Shooter" } ] } EOF |
3.2、生成证书和私钥(其他节点依次生成)
|
1 2 3 4 5 6 7 |
cfssl gencert \ -ca=/root/ssl/etcd/etcd-ca.pem \ -ca-key=/root/ssl/etcd/etcd-ca-key.pem \ -config=/root/ssl/etcd/ca-config.json \ -profile=kubernetes \ /root/ssl/etcd/k8s-master-1.json | \ cfssljson -bare /root/ssl/etcd/etcd-member-k8s-master-1 |
4、创建etcd client证书
4.1、创建证书签名请求:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
cat > /root/ssl/etcd/etcd-client.json << EOF { "CN": "client", "hosts": [""], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "Shooter" } ] } EOF |
4.2、 生成证书和私钥:
|
1 2 3 4 5 6 7 |
cfssl gencert \ -ca=/root/ssl/etcd/etcd-ca.pem \ -ca-key=/root/ssl/etcd/etcd-ca-key.pem \ -config=/root/ssl/etcd/ca-config.json \ -profile=kubernetes \ /root/ssl/etcd/etcd-client.json | \ cfssljson -bare /root/ssl/etcd/etcd-client |
4.3、分发证书( 分发生成的证书和私钥到各 etcd 节点: )
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
# 分发server服务端证书 scp -r /root/ssl/etcd/etcd-server* root@192.168.0.12:/apps/etcd/ssl scp -r /root/ssl/etcd/etcd-server* root@192.168.0.13:/apps/etcd/ssl scp -r /root/ssl/etcd/etcd-server* root@192.168.0.14:/apps/etcd/ssl # 分发192.168.0.12 节点证书 scp -r /root/ssl/etcd/etcd-member-k8s-master-1* root@192.168.0.12:/apps/etcd/ssl # 分发192.168.0.13 节点证书 scp -r /root/ssl/etcd/etcd-member-k8s-master-2* root@192.168.0.13:/apps/etcd/ssl # 分发192.168.0.14 节点证书 scp -r /root/ssl/etcd/etcd-member-k8s-master-3* root@192.168.0.14:/apps/etcd/ssl # 分发client(客户端)证书到K8S master 节点,kube-apiserver 连接etcd 集群使用 scp -r /root/ssl/etcd/etcd-client* root@192.168.0.12:/apps/k8s/ssl/etcd/ scp -r /root/ssl/etcd/etcd-client* root@192.168.0.13:/apps/k8s/ssl/etcd/ scp -r /root/ssl/etcd/etcd-client* root@192.168.0.14:/apps/k8s/ssl/etcd/ |
- 本文固定链接: https://www.yoyoask.com/?p=8398
- 转载请注明: shooter 于 SHOOTER 发表