各个证书的过期时间
|
1 2 3 4 5 6 7 8 9 10 |
/etc/kubernetes/pki/apiserver.crt #1年有效期 /etc/kubernetes/pki/front-proxy-ca.crt #10年有效期 /etc/kubernetes/pki/ca.crt #10年有效期 /etc/kubernetes/pki/apiserver-etcd-client.crt #1年有效期 /etc/kubernetes/pki/front-proxy-client.crt #1年有效期 /etc/kubernetes/pki/etcd/server.crt #1年有效期 /etc/kubernetes/pki/etcd/ca.crt #10年有效期 /etc/kubernetes/pki/etcd/peer.crt #1年有效期 /etc/kubernetes/pki/etcd/healthcheck-client.crt #1年有效期 /etc/kubernetes/pki/apiserver-kubelet-client.crt #1年有效期 |
可用于检查证书过期时间:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# 方法1 kubeadm alpha certs check-expiration # 方法2 openssl x509 -noout -dates -in /etc/kubernetes/pki/apiserver.crt kubeadm alpha certs 命令详解: Available Commands: certificate-key 生成证书和key check-expiration 检测证书过期时间 renew 续订Kubernetes集群的证书 kubeadm alpha certs命令仅支持v1.15及其以上的版本。 kubeadm alpha certs renew all #更新所有证书,慎用 |
手动续订apiserver的证书-apiserver.crt
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
[root@master-63 ~]# kubeadm alpha certs check-expiration [check-expiration] Reading configuration from the cluster... [check-expiration] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -oyaml' CERTIFICATE EXPIRES RESIDUAL TIME CERTIFICATE AUTHORITY EXTERNALLY MANAGED admin.conf May 22, 2021 15:26 UTC 327d no apiserver May 22, 2021 15:26 UTC 327d ca no apiserver-etcd-client May 22, 2021 15:26 UTC 327d etcd-ca no apiserver-kubelet-client May 22, 2021 15:26 UTC 327d ca no controller-manager.conf May 22, 2021 15:26 UTC 327d no etcd-healthcheck-client May 22, 2021 15:26 UTC 327d etcd-ca no etcd-peer May 22, 2021 15:26 UTC 327d etcd-ca no etcd-server May 22, 2021 15:26 UTC 327d etcd-ca no front-proxy-client May 22, 2021 15:26 UTC 327d front-proxy-ca no scheduler.conf May 22, 2021 15:26 UTC 327d no CERTIFICATE AUTHORITY EXPIRES RESIDUAL TIME EXTERNALLY MANAGED ca May 20, 2030 15:26 UTC 9y no etcd-ca May 20, 2030 15:26 UTC 9y no front-proxy-ca May 20, 2030 15:26 UTC 9y no |
当前 apiserver.crt 到期时间是 May 22, 2021 15:26 UTC 剩余327天
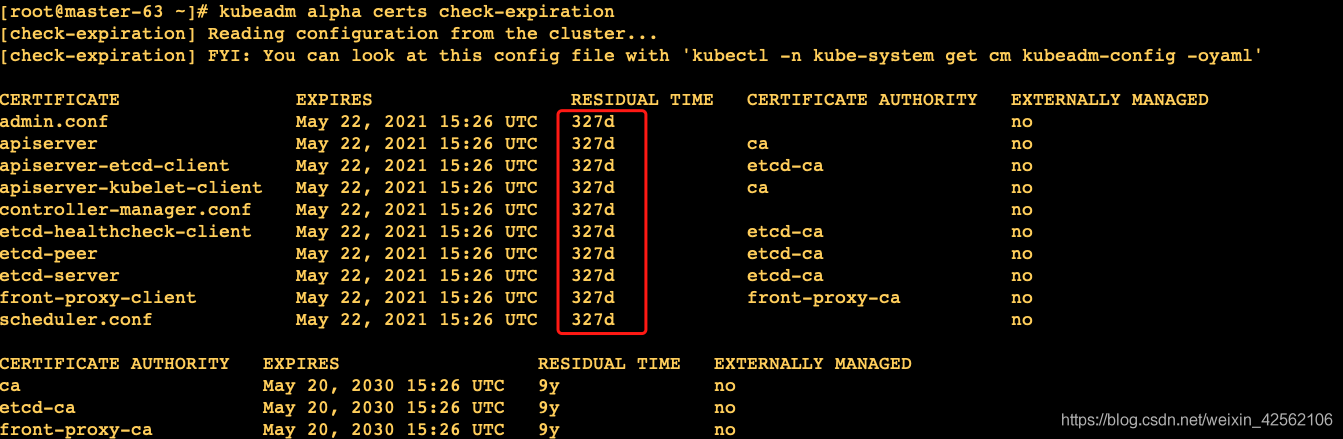
执行renew更新:
|
1 2 3 4 5 6 |
[root@master-63 ~]# kubeadm alpha certs renew apiserver [renew] Reading configuration from the cluster... [renew] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -oyaml' certificate for serving the Kubernetes API renewed |
重启kubelet会自动重新创建核心组件
|
1 |
systemctl restart kubelet |
验证:
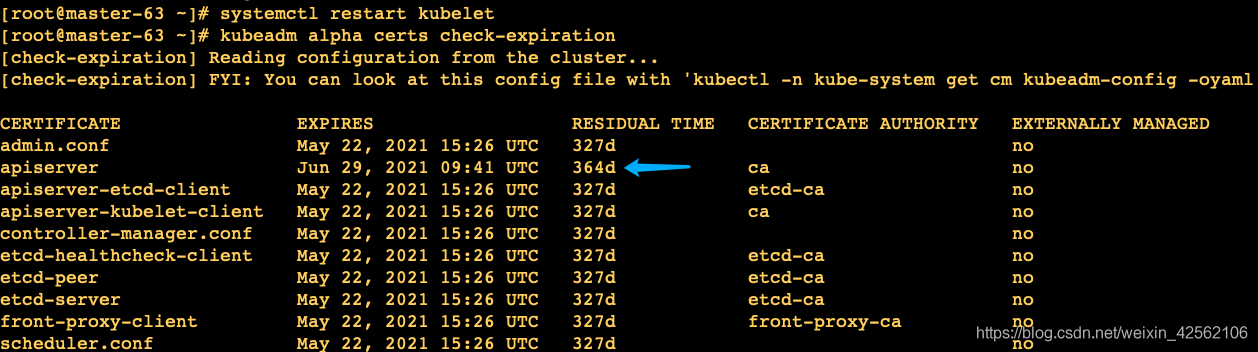
apiserver证书到期时间发生了变化, 不过不是顺延一年, 而是 从你 执行renew成功的时间开始续签一年。
如果要将所有证书续签一年,则执行:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
#kubeadm alpha certs renew all [root@master-63 ~]# kubeadm alpha certs renew all [renew] Reading configuration from the cluster... [renew] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -oyaml' certificate embedded in the kubeconfig file for the admin to use and for kubeadm itself renewed certificate for serving the Kubernetes API renewed certificate the apiserver uses to access etcd renewed certificate for the API server to connect to kubelet renewed certificate embedded in the kubeconfig file for the controller manager to use renewed certificate for liveness probes to healthcheck etcd renewed certificate for etcd nodes to communicate with each other renewed certificate for serving etcd renewed certificate for the front proxy client renewed certificate embedded in the kubeconfig file for the scheduler manager to use renewed |
查看全部估清了

以上结束了.
使用外部CA续订证书
1.生成CSR和私钥:
|
1 2 3 4 |
kubeadm alpha certs renew apiserver --csr-only --csr-dir /tmp/apiserver.csr --csr-only:仅生成CSR。 --csr-dir:生成的CSR和私钥文件保存在哪里,默认保存在/etc/kubernetes/pki |
2.查看CSR和私钥:
命令输出结果中提供了CSR和私钥。
|
1 2 3 |
root@k8s-master:~# ls /tmp/apiserver.csr/ apiserver.csr apiserver.key |
3.使用该私钥到CA上请求签发证书。
|
1 |
将颁发的证书及私钥复制到PKI目录/etc/kubernetes/pki中。 |
参考链接
|
1 |
https://kubernetes.io/zh/docs/reference/setup-tools/kubeadm/kubeadm-alpha/ |

|
1 |
本文转自:https://blog.csdn.net/weixin_42562106/article/details/107025507 |
- 本文固定链接: https://www.yoyoask.com/?p=8352
- 转载请注明: shooter 于 SHOOTER 发表