紧接上文 SSO docker部署 本节来看k8s部署
思路:
- 1.在k8s当中部署Authelia pod
- 2.在traefik当中定义Middleware
- 3.在traefik当中调用Middleware
|
1 |
注意:traefik不要放在kube-system ns下否则可能导致各种奇奇怪怪的无法跳转,没有权限的问题 |
一. 部署Authelia Pod至k8s
|
1 |
这里本认选择挂载配置文件的方式,来部署Authelia pod,因为当前这个配置当中涉及的,配置项较多,有config,有用户列表,有db,所以统一挂载比较快捷。有兴趣的可以配置到configmap和sc当中 |
这里配置的时候,最好不要配置到kube-system这个ns下,因为默认情况下是没有权限去访问kube-system里面的应用的,感谢 @Night Of The Dead 大佬提醒
yaml (注意这里要将authelia的所有配置文件正确挂载,否则无法启动)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 |
apiVersion: v1 kind: Service metadata: labels: app: sso-authelia name: sso-authelia spec: ports: - name: http port: 9091 protocol: TCP targetPort: 9091 nodePort: 9091 selector: app: sso-authelia type: NodePort --- apiVersion: v1 kind: PersistentVolumeClaim metadata: name: authelia-pv-claim spec: storageClassName: nfs accessModes: - ReadWriteMany resources: requests: storage: 1Gi --- apiVersion: apps/v1beta2 kind: Deployment metadata: labels: app: sso-authelia name: sso-authelia spec: replicas: 1 selector: matchLabels: app: sso-authelia template: metadata: labels: app: sso-authelia spec: containers: - image: authelia/authelia name: sso-authelia #args: #- "--config=/config/config.yml" volumeMounts: - name: authelia-configmap mountPath: /config/ ports: - containerPort: 9091 protocol: TCP imagePullSecrets: - name: IfNotPresent volumes: - name: authelia-configmap persistentVolumeClaim: claimName: authelia-pv-claim |
在traefik当中定义authelia的Route [注意不要放在kube-system ns下可能会无法访问or 404]
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: autheus-dashboard-tls spec: entryPoints: - websecure routes: - match: Host(`login.9l988.com`) kind: Rule services: - name: sso-authelia port: 9091 tls: certResolver: ali domains: - main: 9l988.com sans: - '*.9l988.com' |
二. 在traefik当中定义Middleware
参考地址:
|
1 |
https://doc.traefik.io/traefik/v2.2/middlewares/forwardauth/ |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
apiVersion: traefik.containo.us/v1alpha1 kind: Middleware metadata: name: authelia spec: forwardAuth: address: http://sso-authelia.default:9091/api/verify?rd=https://login.9l988.com:9091/ trustForwardHeader: true authResponseHeaders: - "Remote-User" - "Remote-Groups" - "Remote-Name" - "Remote-Email" #注意:address: https://login.9l988.com:9091/ #跳转至这个外部地址去进行验证(authelia) http://sso-authelia.default:9091 #通过svc地址获得进一步验证信息 |
三. 在traefik当中调用Middleware
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: simpleingressroute spec: entryPoints: - websecure routes: - match: HostRegexp(`who.9l988.com`) kind: Rule services: - name: whoami port: 80 middlewares: - name: authelia tls: certResolver: ali domains: - main: "*.9l988.com" |
测试跳转验证:
|
1 |
访问:https://who.9l988.com 访问后自动跳转至验证页面 |
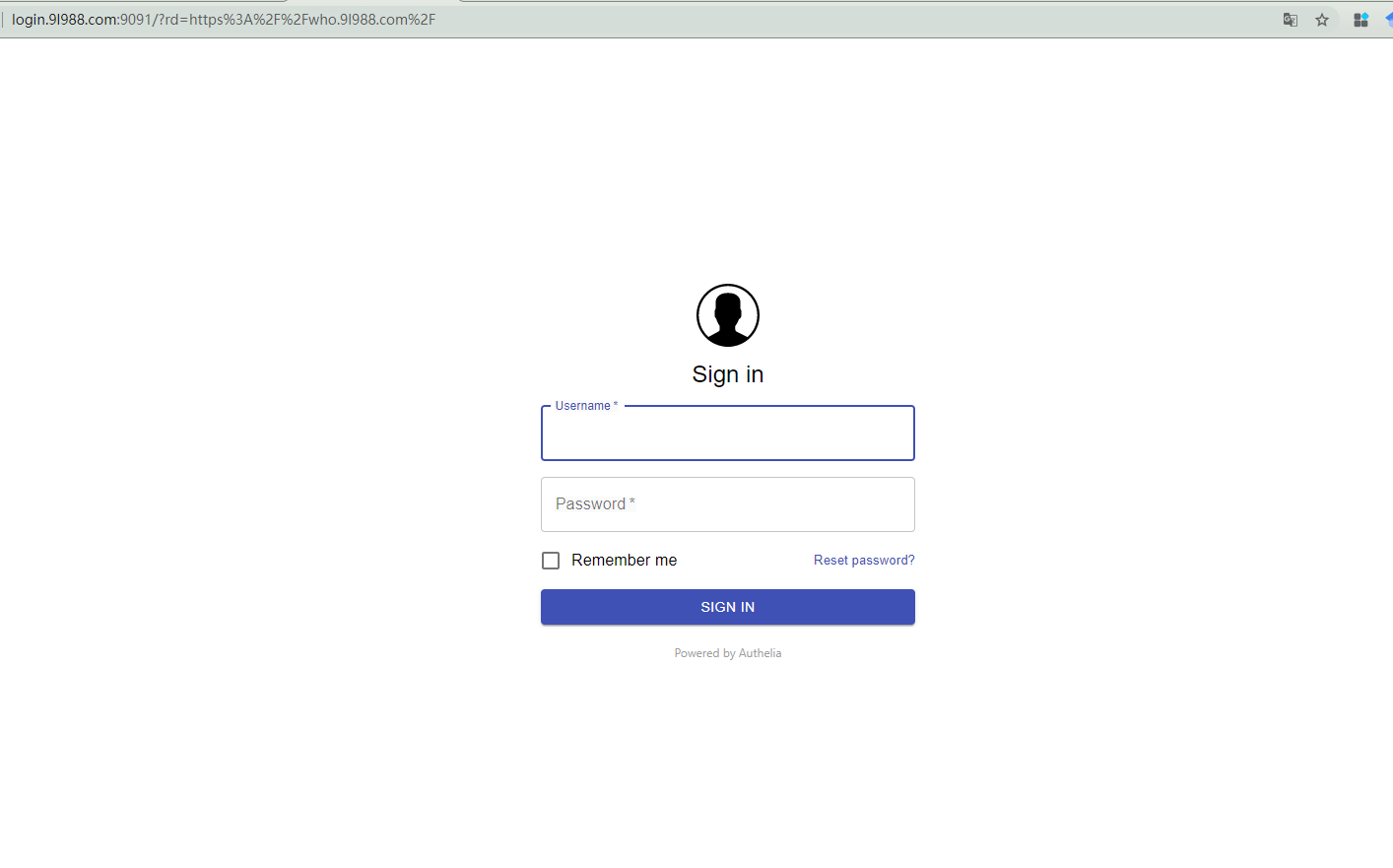
输入账号密码登录:(打印出日志)
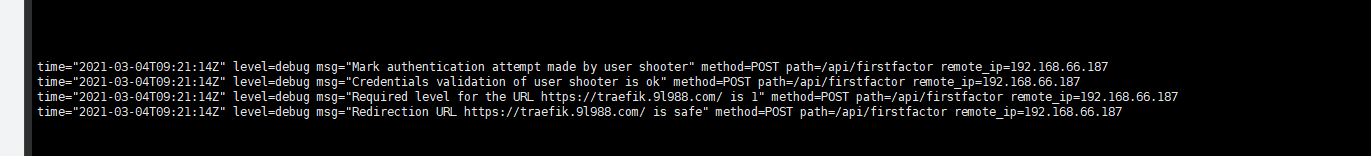
跳转:
注意这里仅支持HTTPS
|
1 |
why: 因为session和cookie只能通过 https传输 |
(待续…)
- 本文固定链接: https://www.yoyoask.com/?p=4763
- 转载请注明: shooter 于 SHOOTER 发表