Qist: https://github.com/qist/k8s/tree/main/k8s-yaml/dashboard
本文按照自签发证书方式部署,官方部署直接执行yaml即可
1、使用cfss签发证书
1.1、工具配置(创建证书的工具)
|
1 2 3 4 5 6 7 8 9 10 |
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 chmod +x cfssl* cp cfssl_linux-amd64 /usr/local/bin/cfssl cp cfssljson_linux-amd64 /usr/local/bin/cfssljson cp cfssl-certinfo_linux-amd64 /usr/local/bin/cfssl-certinfo #创建证书目录 mkdir -p /etc/cfssl/k8s/ mkdir -p /etc/cfssl/pki/k8s/ |
|
1 2 |
mkdir dashboard/tls/ca && cd dashboard/tls/ca vim ca-csr.json |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
{ "CN": "kubernetes", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "system" } ], "ca": { "expiry": "87600h" } } |
|
1 2 3 |
注: CN:Common Name,kube-apiserver 从证书中提取该字段作为请求的用户名 (User Name);浏览器使用该字段验证网站是否合法; O:Organization,kube-apiserver 从证书中提取该字段作为请求用户所属的组 (Group) |
1.2、创建ca证书
|
1 |
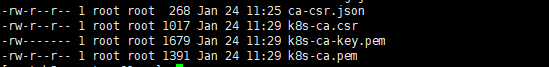
cfssl gencert -initca ca-csr.json | cfssljson -bare k8s-ca |
|
1 |
cp k8s-ca-key.pem k8s-ca.pem /etc/cfssl/pki/k8s/ |
1.3、 配置ca证书策略
|
1 |
vim ca-config.json |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
{ "signing": { "default": { "expiry": "87600h" }, "profiles": { "kubernetes": { "usages": [ "signing", "key encipherment", "server auth", "client auth" ], "expiry": "87600h" } } } } |
|
1 |
cp ca-config.json /etc/cfssl/ |
1.4、配置证书生成脚本,修改HOST_PATH和CERT_PROFILE与你自身匹配
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
#!/bin/bash HOST_PATH="/etc" CERT_PROFILE="kubernetes" cat << EOF | tee ${HOST_PATH}/cfssl/k8s/kubernetes-dashboard.json { "CN": "kubernetes-dashboard", "hosts": [""], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "Shanghai", "L": "Shanghai", "O": "k8s", "OU": "system" } ] } EOF cfssl gencert \ -ca=${HOST_PATH}/cfssl/pki/k8s/k8s-ca.pem \ -ca-key=${HOST_PATH}/cfssl/pki/k8s/k8s-ca-key.pem \ -config=${HOST_PATH}/cfssl/ca-config.json \ -profile=${CERT_PROFILE} \ ${HOST_PATH}/cfssl/k8s/kubernetes-dashboard.json | \ cfssljson -bare ./kubernetes-dashboard cat << EOF | tee ./kubernetes-dashboard-secrets.yaml apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboard type: Opaque data: dashboard.crt: `cat ./kubernetes-dashboard.pem|base64 | tr -d '\n'` dashboard.key: `cat ./kubernetes-dashboard-key.pem|base64 | tr -d '\n'` EOF |
1.5、生成证书
|
1 2 |
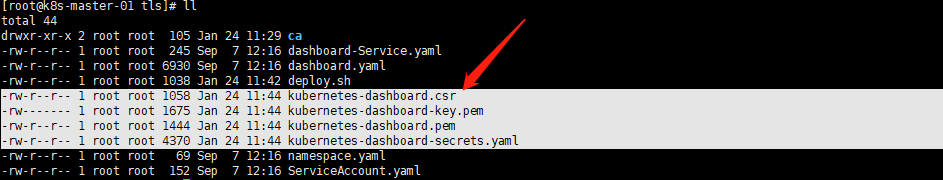
/usr/bin/bash deploy.sh #查看已生成的kubernetes-dashboard-secrets.yaml |
1.6、执行yaml创建
|
1 |
kubectl apply -f . |
|
1 |
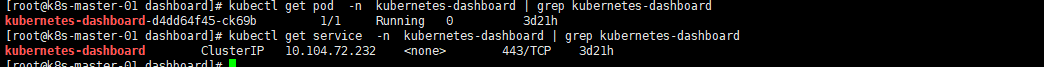
kubectl get pod -n kubernetes-dashboard | grep kubernetes-dashboard kubectl get service -n kubernetes-dashboard | grep kubernetes-dashboard |
2.创建对外访问
Ingress
|
1 2 3 4 |
1.使用Ingress-secret.sh创建Ingress-secret 2.然后运行nginx-dashboard-Ingress.yaml创建对外访问 方便办公网络访问kubernetes-dashboard 一定要使用访问 使用Traefik 提供Ingress 服务 |
2.1 制作ssl证书
|
1 2 3 4 5 6 7 |
cd dashboard/ openssl genrsa -des3 -out server.key 2048 #生成私钥 openssl req -new -key server.key -out server.csr #创建证书请求 cp server.key server.key.org #备份私钥 openssl rsa -in server.key -out server.key #退掉密码 openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt #签名 |
2.2、修改Ingress-secret.sh tls.crt 路径 tls.key 路径
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
#!/bin/bash cat << EOF | tee ./dashboard-tls-cert-secrets.yaml apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: dashboard-tls-cert namespace: kubernetes-dashboard type: Opaque data: tls.crt: `cat ./server.crt | tr -d '\n'` tls.key: `cat ./server.key |base64 | tr -d '\n'` EOF |
2.3、运行脚本,创建ingress secret
|
1 |
/usr/bin/bash Ingress-secret.sh |
2.4、创建ingress.yaml
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
apiVersion: extensions/v1beta1 kind: Ingress metadata: annotations: nginx.ingress.kubernetes.io/backend-protocol: HTTPS nginx.ingress.kubernetes.io/ingress.class: nginx nginx.ingress.kubernetes.io/rewrite-target: / nginx.ingress.kubernetes.io/ssl-redirect: "true" nginx.ingress.kubernetes.io/use-regex: "true" labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: rules: - host: dashboard.shooter.com http: paths: - backend: serviceName: kubernetes-dashboard servicePort: 443 #pathType: ImplementationSpecific #低于19删除这行 tls: - secretName: kubernetes-dashboard-certs #secret |
2.5、执行部署ingress
|
1 2 |
kubectl apply -f dashboard-tls-cert-secrets.yaml kubectl apply -f Ingress.yaml |
2.6、访问
2.7、traefik(推荐 使用Traefik 提供Ingress 服务)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
apiVersion: networking.k8s.io/v1beta1 kind: Ingress metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard annotations: kubernetes.io/ingress.class: traefik traefik.ingress.kubernetes.io/router.entrypoints: websecure traefik.ingress.kubernetes.io/router.tls: "true" spec: rules: - host: dashboard.shooter.com http: paths: - backend: serviceName: kubernetes-dashboard servicePort: 443 tls: - secretName: dashboard-tls-cert #- secretName: dashboard-tls-cert |
3.生成登陆kubeconfig 文件
3.1、执行dashboard-kubeconfig.sh 生成登陆kubeconfig 文件
|
1 2 3 |
修改 HOST_PATH="/etc" #修改为你的ca路径 KUBE_APISERVER="192.168.0.107:6443" #修改为你的api-servser ip和端口 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
#!/bin/bash HOST_PATH="/etc" KUBE_APISERVER="192.168.0.107:6443" #创建 用户 kubectl create sa dashboard-admin -n kube-system # 授权用户 访问权限 kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin #获取token ADMIN_SECRET=$(kubectl get secrets -n kube-system | grep dashboard-admin | awk '{print $1}') #获取dashboard.kubeconfig 使用token 值 DASHBOARD_LOGIN_TOKEN=$(kubectl describe secret -n kube-system ${ADMIN_SECRET} | grep -E '^token' | awk '{print $2}') echo ${DASHBOARD_LOGIN_TOKEN} kubectl config set-cluster kubernetes \ --certificate-authority=${HOST_PATH}/cfssl/pki/k8s/k8s-ca.pem \ --embed-certs=true \ --server=${KUBE_APISERVER} \ --kubeconfig=dashboard.kubeconfig # 设置客户端认证参数,使用上面创建的 Token kubectl config set-credentials dashboard_user \ --token=${DASHBOARD_LOGIN_TOKEN} \ --kubeconfig=dashboard.kubeconfig # 设置上下文参数 kubectl config set-context default \ --cluster=kubernetes \ --user=dashboard_user \ --kubeconfig=dashboard.kubeconfig # 设置默认上下文 kubectl config use-context default --kubeconfig=dashboard.kubeconfig |
3.2、执行生成
|
1 |
/usr/bin/bash dashboard-kubeconfig.sh |
生成dashboard.kubeconfig文件并登录

(完成)
- 本文固定链接: https://www.yoyoask.com/?p=7295
- 转载请注明: shooter 于 SHOOTER 发表