安装
|
1 2 3 4 5 6 7 8 9 10 11 |
#yum安装的话需要设置源 curl -L https://packages.gitlab.com/install/repositories/runner/gitlab-ci-multi-runner/script.rpm.sh | sudo bash #查看gitlab版本 cat /opt/gitlab/embedded/service/gitlab-rails/VERSION #获取相关版本的rpm包 https://mirrors.tuna.tsinghua.edu.cn/gitlab-runner/yum/el7/ #下载的镜像源要对应你爹gitlab版本 yum install https://mirrors.tuna.tsinghua.edu.cn/gitlab-runner/yum/el7/gitlab-runner-12.3.0-1.x86_64.rpm |
注册
http注册:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
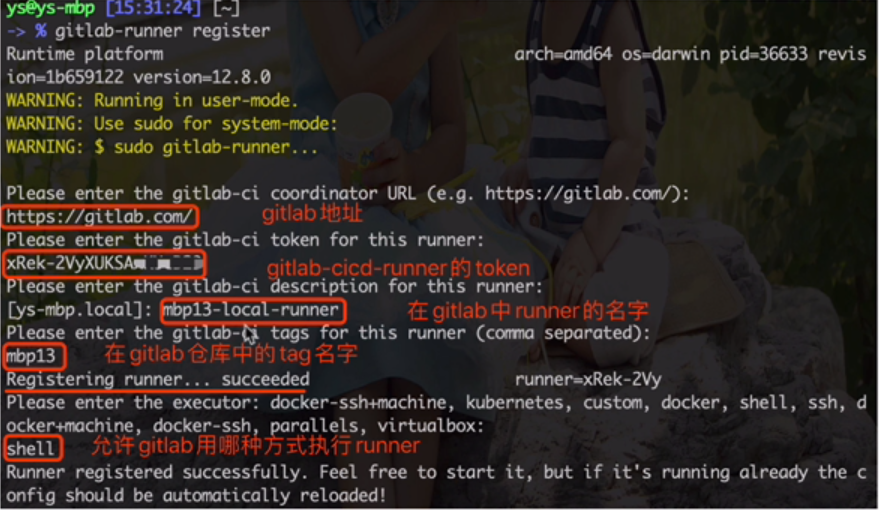
#注意这种方式注册后的runner是带锁的locked (locked作用:锁定runner到当前项目,当运行程序被锁定时,它不能分配给其他项目) gitlab-ci-multi-runner register #加上locked参数就不会锁 gitlab-runner register --locked="false" [root@minio1 piggymetrics-master]# gitlab-runner register --locked="false" WARN[0000] boolean parameters must be passed in the command line with --locked=false WARN[0000] parameters after this may be ignored Runtime platform arch=amd64 os=linux pid=53999 revision=a8a019e0 version=12.3.0 Running in system-mode. Please enter the gitlab-ci coordinator URL (e.g. https://gitlab.com/): http://gitlab.shooter.com Please enter the gitlab-ci token for this runner: 22QvxHDw8p7x36N_tGoL Please enter the gitlab-ci description for this runner: [minio1]: my-demo1 Please enter the gitlab-ci tags for this runner (comma separated): #(很重要,在.gitlab-ci.yml文件里面指定tags,匹哪个tags可以使用本runner)这里键入的标签,会匹配gitlab-ci.yml文件当中job任务的tags标签来决定是否运行 Registering runner... succeeded runner=22QvxHDw #选择执行器 Please enter the executor: docker-ssh, parallels, virtualbox, kubernetes, docker, shell, ssh, docker+machine, docker-ssh+machine, custom: docker Enter the default Docker image (for example, ruby:2.6): prokop7/maven3.6.1-jdk11 #这里定义编译你程序所需的环境镜像版本 Runner registered successfully. Feel free to start it, but if it's running already the config should be automatically reloaded! |
另一种注册方式:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
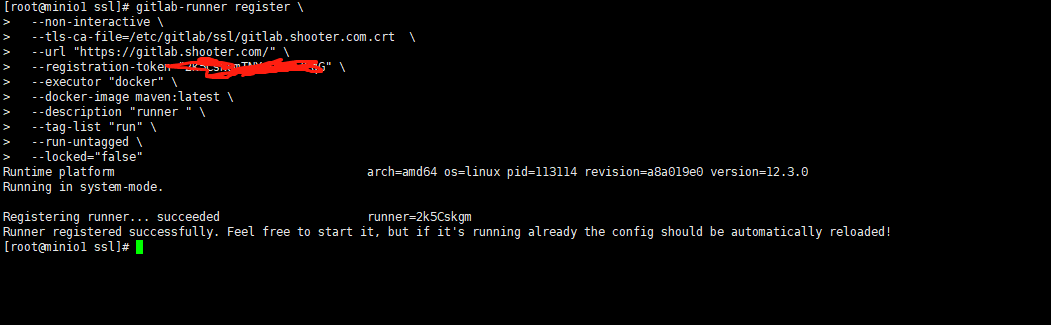
gitlab-runner register \ --non-interactive \ --url "http://gitlab.shooter.com/" \ --registration-token "2k5CskgmTNxxxxxx" \ --executor "shell" \ --docker-image maven:latest \ --description "my-runner" \ --tag-list "build,test,deploy" \ #很重要,在.gitlab-ci.yml文件里面指定tags,匹配哪些个tags可以使用此runner --run-untagged \ --locked="false" #完整版如下: gitlab-runner register \ --non-interactive \ --url "http://gitlab.shooter.com/" \ --registration-token "222222xHDw8p7x36N_tGoL" \ --executor "shell" \ --description "local-runner" \ --tag-list "build,test,deploy" \ --run-untagged \ --locked="false" \ --access-level="not_protected" |
http手动注册方式
https注册可能会遇到如下错误
|
1 2 |
ERROR: Registering runner... failed runner=2k5Cskgm status=couldn't execute POST against https://gitlab.shooter.com/api/v4/runners: Post https://gitlab.shooter.com/api/v4/runners: x509: certificate signed by unknown authority PANIC: Failed to register this runner. Perhaps you are having network problems |
解决办法如下
https注册使用如下,因为生成的证书不被认可
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
#适用于本地二进制安装的gitlab-runner gitlab-runner register \ --non-interactive \ --tls-ca-file=/etc/gitlab/ssl/gitlab.shooter.com.crt \ --url "https://gitlab.shooter.com/" \ --registration-token "2k5CskgmTNxxxxxx" \ --executor "shell" \ --docker-image maven:latest \ --description "my-runner" \ --tag-list "build,test,deploy" \ --run-untagged \ --locked="false" #适用于本地二进制安装但是打算用容器镜像打包的(可以很好的做到资源隔离) gitlab-runner register \ --non-interactive \ --tls-ca-file=/etc/gitlab-runner/ssl/gitlab.shooter.com.crt \ --url "https://gitlab.shooter.com/" \ --registration-token "CUsAR21RcVJmyGB" \ --executor "docker" \ --docker-image "registry.cn-shanghai.aliyuncs.com/shooer/jdk-maven-docker-ansible-nodejs:v3.0" \ --description "xmb-test-bae" \ --tag-list "publicrunner" \ --docker-volumes "/var/run/docker.sock:/var/run/docker.sock" \ --docker-volumes "/etc/hosts:/etc/hosts" \ --docker-volumes "/opt/ansible/app1/ansible:/etc/ansible" \ --docker-volumes "/opt/test_script/script:/opt/script" \ --docker-volumes "/opt/maven-repertory:/opt/apache-maven-3.8.1/maven-repertory" \ --run-untagged \ --locked="false" 挂载了本地host,ansible,maven等,启动的那一瞬间就挂载进去 |
注册成功
将gitlab-runner用户添加到docker组
|
1 2 |
sudo gpasswd -a gitlab-runner docker #则是将一个用户加入到另一个组 同时不改变用户原来的组 sudo usermod -aG docker gitlab-runner #改写用户的组之后 如果用户同时属于多个组 那么最终只会属于一个组 |
验证
|
1 |
sudo -u gitlab-runner -H docker info |
docker容器部署gitlab-runner
|
1 |
在开始之前,请确保已安装docker, 本示例将本地系统用于安装到gitlab-runner容器中的配置卷。该卷用于配置和其他资源。 |
使用Docker卷启动Runner容器
1 创建Docker卷:
|
1 |
docker volume create gitlab-runner-config |
2.启动runner( 使用我们刚创建的卷启动GitLab Runner容器,不启动后面注册上后gitlabrunner页面会显示无法连接)
|
1 2 3 4 5 6 |
docker run -d -it --name gitlab-runner --restart always \ -v gitlab-runner-config:/etc/gitlab-runner \ -v /etc/gitlab/ssl:/etc/gitlab-runner/certs \ -v /var/run/docker.sock:/var/run/docker.sock \ -v /etc/hosts:/etc/hosts \ gitlab/gitlab-runner:v15.11.0 |
3.注册runner
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
https:(亲测可用) 本地SSL模式启动,需要把cert文件挂载进去,当然还有宿主机hosts,因为域名是映射在本地(否则后面注册runner,url无法请求gitlab域名,会导致失败) docker run --rm -v gitlab-runner-config:/etc/gitlab-runner -v /etc/gitlab/ssl:/etc/gitlab-runner/certs -v /etc/hosts:/etc/hosts gitlab/gitlab-runner:v15.11.0 register \ --non-interactive \ --tls-ca-file=/etc/gitlab-runner/certs/gitlab.shooter.com.crt \ --url "https://gitlab.shooter.com/" \ --registration-token "4wsz1YvR4rx8eDsgEqbM" \ --executor "docker" \ --docker-image "registry.cn-shanghai.aliyuncs.com/shooer/jdk-maven-docker-ansible-nodejs:v1.0" \ --description "xmb-test" \ --tag-list "publicrunner" \ --run-untagged="true" \ --locked="false" \ --docker-volumes /var/run/docker.sock:/var/run/docker.sock \ --docker-volumes /etc/hosts:/etc/hosts \ --access-level="not_protected" \ --docker-pull-policy="if-not-present" ###其中 --docker-volumes /var/run/docker.sock:/var/run/docker.sock \ --docker-volumes /etc/hosts:/etc/hosts \ 这些挂载映射是将容器内的,就是上面第一步启动的容器runner内的这些路径,挂载到 docker-image "registry.cn-shanghai.aliyuncs.com/shooer/jdk-maven-docker-ansible-nodejs:v1.0" \ 这个镜像里去运行。第一步启动的那个容器runner可以看作是宿主机。 |

gitlab-runner 文档
|
1 2 |
https://docs.gitlab.com/runner/executors/README.html https://wenku.baidu.com/view/f518436b2d3f5727a5e9856a561252d380eb2004.html?_wkts_=1690507473617&bdQuery=gitlab-runner%E9%85%8D%E7%BD%AE%E6%96%87%E4%BB%B6%E8%A7%A3%E6%9E%90 |
其他注册方式
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 |
http:(推荐)(本地模式要带host) docker run --rm -v /etc/gitlab-runner:/etc/gitlab-runner -v /etc/hosts:/etc/hosts gitlab/gitlab-runner register \ --non-interactive \ --executor "docker" \ --docker-image maven3.6.1-jdk11 \ --url "http://gitlab.shooter.com/" \ --registration-token "P43h9m9JrsyDoucsfoVh" \ --description "minio2-runner" \ --tag-list "aliyun" \ --run-untagged="true" \ #运行没有标签的job? 共享runner可以打开 --locked="false" \ --access-level="not_protected" #设置访问等级 not_protected or ref_protected; 默认 not_protected https:(本地模式要带host和ssl) docker run --rm -v /etc/gitlab-runner:/etc/gitlab-runner gitlab/gitlab-runner register \ --tls-ca-file=/etc/gitlab/ssl/gitlab.example.com.crt \ --url https://gitlab.shooter.com/ \ --registration-token P43h9m9JrsyDoucsfoVh \ --tag-list aliyun \ --executor docker \ --docker-image maven3.6.1-jdk11 \ --docker-volumes /etc/gitlab-runner:/etc/gitlab-runner \ --docker-volumes /var/run/docker.sock:/var/run/docker.sock \ --docker-volumes /etc/hosts:/etc/hosts \ --docker-volumes /etc/gitlab/ssl:/etc/gitlab/ssl \ --description "minio2-runner" |
常见错误:
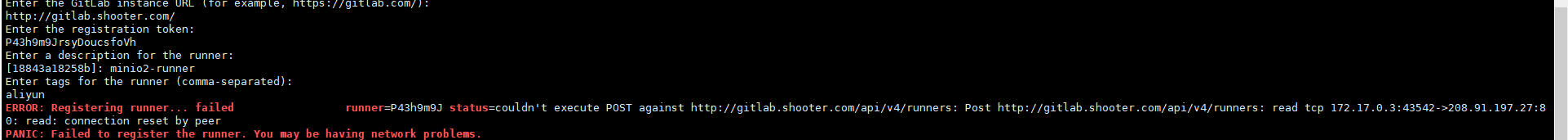
|
1 2 |
ERROR: Registering runner... failed runner=P43h9m9J status=couldn't execute POST against http://gitlab.shooter.com/api/v4/runners: Post http://gitlab.shooter.com/api/v4/runners: read tcp 172.17.0.3:43542->208.91.197.27:80: read: connection reset by peer PANIC: Failed to register the runner. You may be having network problems. |
|
1 |
原因:gitlab-runner容器中无法访问本地域名,说明白就是你没有将宿主机hosts文件映射到容器中(正规线上域名解析的除外,不用做映射)。导致无法访问gitlab服务。 |
|
1 |
runner运行的时候,会先去拉你设置的 --docker-image maven3.6.1-jdk11 \ |
注意:如果您想创建的GitLab Runner给所有GitLab仓库使用,就要创建shared类型;那么token就要去获取全局页面的
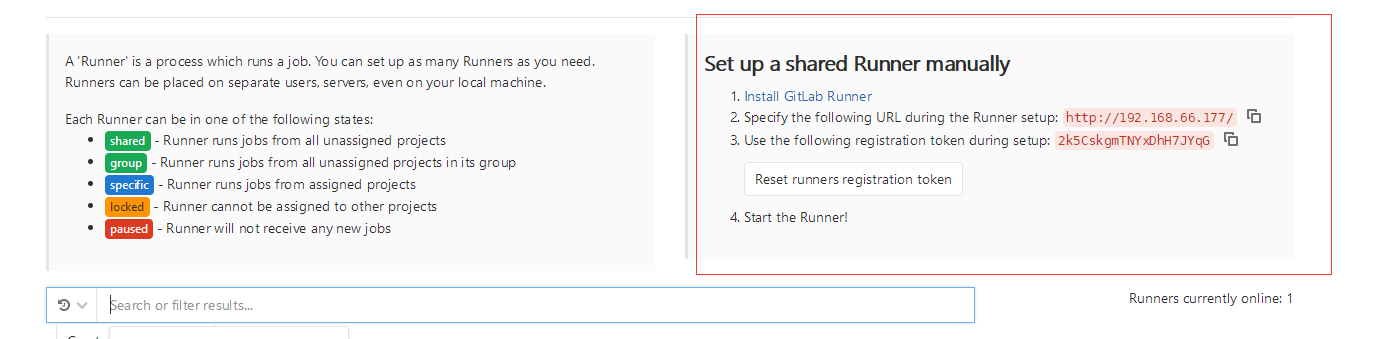
如果您的GitLab Runner只用于给某个固定的Gitlab仓库,就要创建specific类型;就去项目内部获取
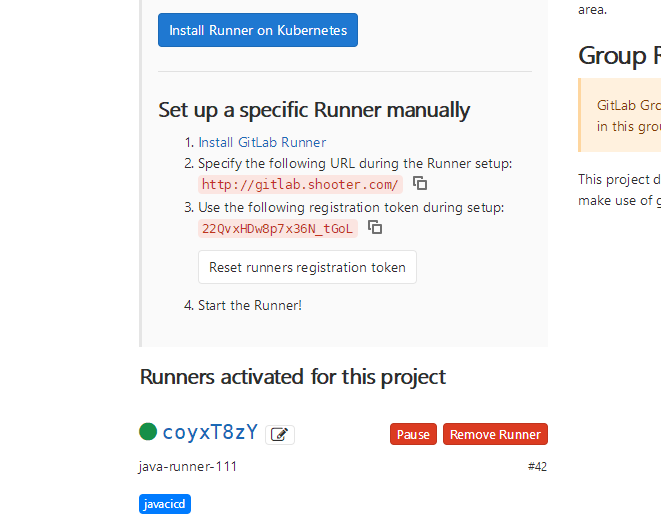
相关命令
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
gitlab-runner register #交互式注册,非交互式添加--non-interactive gitlab-runner list #列出保存在配置文件中的所有运行程序 gitlab-runner verify $检查runner是否可以连接 gitlab-runner unregister #取消已注册的runner #使用令牌注销 gitlab-runner unregister --url http://gitlab.shooter.com --token t0ddsl #使用名称注销(同名删除第一个) gitlab-runner unregister --name test-runner #注销所哟 gitlab-runner unregister --all-runners |
|
1 2 |
gitlab-runner \ --docker的一些参数如下 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 |
OPTIONS: -c value, --config value Config file (default: "/etc/gitlab-runner/config.toml") [$CONFIG_FILE] --template-config value Path to the configuration template file [$TEMPLATE_CONFIG_FILE] --tag-list value Tag list (default: "publicrunner") [$RUNNER_TAG_LIST] -n, --non-interactive Run registration unattended [$REGISTER_NON_INTERACTIVE] --leave-runner Don't remove runner if registration fails [$REGISTER_LEAVE_RUNNER] -r value, --registration-token value Runner's registration token (default: "GR1348941Yg5JfnJMxygZyuWExViT") [$REGISTRATION_TOKEN] --run-untagged Register to run untagged builds; defaults to 'true' when 'tag-list' is empty [$REGISTER_RUN_UNTAGGED] --locked Lock Runner for current project, defaults to 'true' [$REGISTER_LOCKED] --access-level value Set access_level of the runner to not_protected or ref_protected; defaults to not_protected [$REGISTER_ACCESS_LEVEL] --maximum-timeout value What is the maximum timeout (in seconds) that will be set for job when using this Runner (default: "0") [$REGISTER_MAXIMUM_TIMEOUT] --paused Set Runner to be paused, defaults to 'false' [$REGISTER_PAUSED] --maintenance-note value Runner's maintenance note [$REGISTER_MAINTENANCE_NOTE] --name value, --description value Runner name (default: "kedu-ddm-server1") [$RUNNER_NAME] --limit value Maximum number of builds processed by this runner (default: "0") [$RUNNER_LIMIT] --output-limit value Maximum build trace size in kilobytes (default: "0") [$RUNNER_OUTPUT_LIMIT] --request-concurrency value Maximum concurrency for job requests (default: "0") [$RUNNER_REQUEST_CONCURRENCY] -u value, --url value Runner URL (default: "http://gitlab.example.com:82/") [$CI_SERVER_URL] -t value, --token value Runner token [$CI_SERVER_TOKEN] --tls-ca-file value File containing the certificates to verify the peer when using HTTPS [$CI_SERVER_TLS_CA_FILE] --tls-cert-file value File containing certificate for TLS client auth when using HTTPS [$CI_SERVER_TLS_CERT_FILE] --tls-key-file value File containing private key for TLS client auth when using HTTPS [$CI_SERVER_TLS_KEY_FILE] --executor value Select executor, eg. shell, docker, etc. (default: "docker") [$RUNNER_EXECUTOR] --builds-dir value Directory where builds are stored [$RUNNER_BUILDS_DIR] --cache-dir value Directory where build cache is stored [$RUNNER_CACHE_DIR] --clone-url value Overwrite the default URL used to clone or fetch the git ref [$CLONE_URL] --env value Custom environment variables injected to build environment [$RUNNER_ENV] --pre-clone-script value Runner-specific command script executed before code is pulled [$RUNNER_PRE_CLONE_SCRIPT] --post-clone-script value Runner-specific command script executed just after code is pulled [$RUNNER_POST_CLONE_SCRIPT] --pre-build-script value Runner-specific command script executed just before build executes [$RUNNER_PRE_BUILD_SCRIPT] --post-build-script value Runner-specific command script executed just after build executes [$RUNNER_POST_BUILD_SCRIPT] --debug-trace-disabled When set to true Runner will disable the possibility of using the CI_DEBUG_TRACE feature [$RUNNER_DEBUG_TRACE_DISABLED] --shell value Select bash, sh, cmd, pwsh or powershell [$RUNNER_SHELL] --custom_build_dir-enabled Enable job specific build directories [$CUSTOM_BUILD_DIR_ENABLED] --cache-type value Select caching method [$CACHE_TYPE] --cache-path value Name of the path to prepend to the cache URL [$CACHE_PATH] --cache-shared Enable cache sharing between runners. [$CACHE_SHARED] --cache-s3-server-address value A host:port to the used S3-compatible server [$CACHE_S3_SERVER_ADDRESS] --cache-s3-access-key value S3 Access Key [$CACHE_S3_ACCESS_KEY] --cache-s3-secret-key value S3 Secret Key [$CACHE_S3_SECRET_KEY] --cache-s3-bucket-name value Name of the bucket where cache will be stored [$CACHE_S3_BUCKET_NAME] --cache-s3-bucket-location value Name of S3 region [$CACHE_S3_BUCKET_LOCATION] --cache-s3-insecure Use insecure mode (without https) [$CACHE_S3_INSECURE] --cache-s3-authentication_type value IAM or credentials [$CACHE_S3_AUTHENTICATION_TYPE] --cache-gcs-access-id value ID of GCP Service Account used to access the storage [$CACHE_GCS_ACCESS_ID] --cache-gcs-private-key value Private key used to sign GCS requests [$CACHE_GCS_PRIVATE_KEY] --cache-gcs-credentials-file value File with GCP credentials, containing AccessID and PrivateKey [$GOOGLE_APPLICATION_CREDENTIALS] --cache-gcs-bucket-name value Name of the bucket where cache will be stored [$CACHE_GCS_BUCKET_NAME] --cache-azure-account-name value Account name for Azure Blob Storage [$CACHE_AZURE_ACCOUNT_NAME] --cache-azure-account-key value Access key for Azure Blob Storage [$CACHE_AZURE_ACCOUNT_KEY] --cache-azure-container-name value Name of the Azure container where cache will be stored [$CACHE_AZURE_CONTAINER_NAME] --cache-azure-storage-domain value Domain name of the Azure storage (e.g. blob.core.windows.net) [$CACHE_AZURE_STORAGE_DOMAIN] --feature-flags value Enable/Disable feature flags https://docs.gitlab.com/runner/configuration/feature-flags.html (default: "{}") [$FEATURE_FLAGS] --ssh-user value User name [$SSH_USER] --ssh-password value User password [$SSH_PASSWORD] --ssh-host value Remote host [$SSH_HOST] --ssh-port value Remote host port [$SSH_PORT] --ssh-identity-file value Identity file to be used [$SSH_IDENTITY_FILE] --ssh-disable-strict-host-key-checking value Disable SSH strict host key checking [$DISABLE_STRICT_HOST_KEY_CHECKING] --ssh-known-hosts-file value Location of known_hosts file. Defaults to ~/.ssh/known_hosts [$KNOWN_HOSTS_FILE] --docker-host value Docker daemon address [$DOCKER_HOST] --docker-cert-path value Certificate path [$DOCKER_CERT_PATH] --docker-tlsverify Use TLS and verify the remote [$DOCKER_TLS_VERIFY] --docker-hostname value Custom container hostname [$DOCKER_HOSTNAME] --docker-image value Docker image to be used (default: "registry.cn-shanghai.aliyuncs.com/shooer/jdk-maven-docker-ansible-nodejs:v4.0") [$DOCKER_IMAGE] --docker-runtime value Docker runtime to be used [$DOCKER_RUNTIME] --docker-memory value Memory limit (format: <number>[<unit>]). Unit can be one of b, k, m, or g. Minimum is 4M. [$DOCKER_MEMORY] --docker-memory-swap value Total memory limit (memory + swap, format: <number>[<unit>]). Unit can be one of b, k, m, or g. [$DOCKER_MEMORY_SWAP] --docker-memory-reservation value Memory soft limit (format: <number>[<unit>]). Unit can be one of b, k, m, or g. [$DOCKER_MEMORY_RESERVATION] --docker-cpuset-cpus value String value containing the cgroups CpusetCpus to use [$DOCKER_CPUSET_CPUS] --docker-cpus value Number of CPUs [$DOCKER_CPUS] --docker-cpu-shares value Number of CPU shares (default: "0") [$DOCKER_CPU_SHARES] --docker-dns value A list of DNS servers for the container to use [$DOCKER_DNS] --docker-dns-search value A list of DNS search domains [$DOCKER_DNS_SEARCH] --docker-privileged Give extended privileges to container [$DOCKER_PRIVILEGED] --docker-disable-entrypoint-overwrite Disable the possibility for a container to overwrite the default image entrypoint [$DOCKER_DISABLE_ENTRYPOINT_OVERWRITE] --docker-userns value User namespace to use [$DOCKER_USERNS_MODE] --docker-cap-add value Add Linux capabilities [$DOCKER_CAP_ADD] --docker-cap-drop value Drop Linux capabilities [$DOCKER_CAP_DROP] --docker-oom-kill-disable Do not kill processes in a container if an out-of-memory (OOM) error occurs [$DOCKER_OOM_KILL_DISABLE] --docker-oom-score-adjust value Adjust OOM score (default: "0") [$DOCKER_OOM_SCORE_ADJUST] --docker-security-opt value Security Options [$DOCKER_SECURITY_OPT] --docker-devices value Add a host device to the container [$DOCKER_DEVICES] --docker-gpus value Request GPUs to be used by Docker [$DOCKER_GPUS] --docker-disable-cache Disable all container caching [$DOCKER_DISABLE_CACHE] --docker-volumes value Bind-mount a volume and create it if it doesn't exist prior to mounting. Can be specified multiple times once per mountpoint, e.g. --docker-volumes 'test0:/test0' --docker-volumes 'test1:/test1' [$DOCKER_VOLUMES] --docker-volume-driver value Volume driver to be used [$DOCKER_VOLUME_DRIVER] --docker-cache-dir value Directory where to store caches [$DOCKER_CACHE_DIR] --docker-extra-hosts value Add a custom host-to-IP mapping [$DOCKER_EXTRA_HOSTS] --docker-volumes-from value A list of volumes to inherit from another container [$DOCKER_VOLUMES_FROM] --docker-network-mode value Add container to a custom network [$DOCKER_NETWORK_MODE] --docker-links value Add link to another container [$DOCKER_LINKS] --docker-wait-for-services-timeout value How long to wait for service startup (default: "0") [$DOCKER_WAIT_FOR_SERVICES_TIMEOUT] --docker-allowed-images value Image allowlist [$DOCKER_ALLOWED_IMAGES] --docker-allowed-services value Service allowlist [$DOCKER_ALLOWED_SERVICES] --docker-pull-policy value Image pull policy: never, if-not-present, always [$DOCKER_PULL_POLICY] --docker-shm-size value Shared memory size for docker images (in bytes) (default: "0") [$DOCKER_SHM_SIZE] --docker-tmpfs value A toml table/json object with the format key=values. When set this will mount the specified path in the key as a tmpfs volume in the main container, using the options specified as key. For the supported options, see the documentation for the unix 'mount' command (default: "{}") [$DOCKER_TMPFS] --docker-services-tmpfs value A toml table/json object with the format key=values. When set this will mount the specified path in the key as a tmpfs volume in all the service containers, using the options specified as key. For the supported options, see the documentation for the unix 'mount' command (default: "{}") [$DOCKER_SERVICES_TMPFS] --docker-sysctls value Sysctl options, a toml table/json object of key=value. Value is expected to be a string. (default: "{}") [$DOCKER_SYSCTLS] --docker-helper-image value [ADVANCED] Override the default helper image used to clone repos and upload artifacts [$DOCKER_HELPER_IMAGE] --docker-helper-image-flavor value Set helper image flavor (alpine, ubuntu), defaults to alpine [$DOCKER_HELPER_IMAGE_FLAVOR] --docker-container-labels value A toml table/json object of key-value. Value is expected to be a string. When set, this will create containers with the given container labels. Environment variables will be substituted for values here. (default: "{}") --parallels-base-name value VM name to be used [$PARALLELS_BASE_NAME] --parallels-template-name value VM template to be created [$PARALLELS_TEMPLATE_NAME] --parallels-disable-snapshots Disable snapshoting to speedup VM creation [$PARALLELS_DISABLE_SNAPSHOTS] --parallels-time-server value Timeserver to sync the guests time from. Defaults to time.apple.com [$PARALLELS_TIME_SERVER] --parallels-allowed-images value Image (base_name) allowlist [$PARALLELS_ALLOWED_IMAGES] --virtualbox-base-name value VM name to be used [$VIRTUALBOX_BASE_NAME] --virtualbox-base-snapshot value Name or UUID of a specific VM snapshot to clone [$VIRTUALBOX_BASE_SNAPSHOT] --virtualbox-base-folder value Folder in which to save the new VM. If empty, uses VirtualBox default [$VIRTUALBOX_BASE_FOLDER] --virtualbox-disable-snapshots Disable snapshoting to speedup VM creation [$VIRTUALBOX_DISABLE_SNAPSHOTS] --virtualbox-allowed-images value Image allowlist [$VIRTUALBOX_ALLOWED_IMAGES] --machine-max-growth-rate value Maximum machines being provisioned concurrently, set to 0 for unlimited (default: "0") [$MACHINE_MAX_GROWTH_RATE] --machine-idle-nodes value Maximum idle machines (default: "0") [$MACHINE_IDLE_COUNT] --machine-idle-scale-factor value (Experimental) Defines what factor of in-use machines should be used as current idle value, but never more then defined IdleCount. 0.0 means use IdleCount as a static number (defaults to 0.0). Must be defined as float number. (default: "0") [$MACHINE_IDLE_SCALE_FACTOR] --machine-idle-count-min value Minimal number of idle machines when IdleScaleFactor is in use. Defaults to 1. (default: "0") [$MACHINE_IDLE_COUNT_MIN] --machine-idle-time value Minimum time after node can be destroyed (default: "0") [$MACHINE_IDLE_TIME] --machine-max-builds value Maximum number of builds processed by machine (default: "0") [$MACHINE_MAX_BUILDS] --machine-machine-driver value The driver to use when creating machine [$MACHINE_DRIVER] --machine-machine-name value The template for machine name (needs to include %s) [$MACHINE_NAME] --machine-machine-options value Additional machine creation options [$MACHINE_OPTIONS] --kubernetes-host value Optional Kubernetes master host URL (auto-discovery attempted if not specified) [$KUBERNETES_HOST] --kubernetes-cert-file value Optional Kubernetes master auth certificate [$KUBERNETES_CERT_FILE] --kubernetes-key-file value Optional Kubernetes master auth private key [$KUBERNETES_KEY_FILE] --kubernetes-ca-file value Optional Kubernetes master auth ca certificate [$KUBERNETES_CA_FILE] --kubernetes-bearer_token_overwrite_allowed Bool to authorize builds to specify their own bearer token for creation. [$KUBERNETES_BEARER_TOKEN_OVERWRITE_ALLOWED] --kubernetes-bearer_token value Optional Kubernetes service account token used to start build pods. [$KUBERNETES_BEARER_TOKEN] --kubernetes-image value Default docker image to use for builds when none is specified [$KUBERNETES_IMAGE] --kubernetes-namespace value Namespace to run Kubernetes jobs in [$KUBERNETES_NAMESPACE] --kubernetes-namespace_overwrite_allowed value Regex to validate 'KUBERNETES_NAMESPACE_OVERWRITE' value [$KUBERNETES_NAMESPACE_OVERWRITE_ALLOWED] --kubernetes-privileged value Run all containers with the privileged flag enabled [$KUBERNETES_PRIVILEGED] --kubernetes-runtime-class-name value A Runtime Class to use for all created pods, errors if the feature is unsupported by the cluster [$KUBERNETES_RUNTIME_CLASS_NAME] --kubernetes-allow-privilege-escalation value Run all containers with the security context allowPrivilegeEscalation flag enabled. When empty, it does not define the allowPrivilegeEscalation flag in the container SecurityContext and allows Kubernetes to use the default privilege escalation behavior. [$KUBERNETES_ALLOW_PRIVILEGE_ESCALATION] --kubernetes-cpu-limit value The CPU allocation given to build containers [$KUBERNETES_CPU_LIMIT] --kubernetes-cpu-limit-overwrite-max-allowed value If set, the max amount the cpu limit can be set to. Used with the KUBERNETES_CPU_LIMIT variable in the build. [$KUBERNETES_CPU_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-cpu-request value The CPU allocation requested for build containers [$KUBERNETES_CPU_REQUEST] --kubernetes-cpu-request-overwrite-max-allowed value If set, the max amount the cpu request can be set to. Used with the KUBERNETES_CPU_REQUEST variable in the build. [$KUBERNETES_CPU_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-memory-limit value The amount of memory allocated to build containers [$KUBERNETES_MEMORY_LIMIT] --kubernetes-memory-limit-overwrite-max-allowed value If set, the max amount the memory limit can be set to. Used with the KUBERNETES_MEMORY_LIMIT variable in the build. [$KUBERNETES_MEMORY_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-memory-request value The amount of memory requested from build containers [$KUBERNETES_MEMORY_REQUEST] --kubernetes-memory-request-overwrite-max-allowed value If set, the max amount the memory request can be set to. Used with the KUBERNETES_MEMORY_REQUEST variable in the build. [$KUBERNETES_MEMORY_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-ephemeral-storage-limit value The amount of ephemeral storage allocated to build containers [$KUBERNETES_EPHEMERAL_STORAGE_LIMIT] --kubernetes-ephemeral-storage-limit-overwrite-max-allowed value If set, the max amount the ephemeral limit can be set to. Used with the KUBERNETES_EPHEMERAL_STORAGE_LIMIT variable in the build. [$KUBERNETES_EPHEMERAL_STORAGE_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-ephemeral-storage-request value The amount of ephemeral storage requested from build containers [$KUBERNETES_EPHEMERAL_STORAGE_REQUEST] --kubernetes-ephemeral-storage-request-overwrite-max-allowed value If set, the max amount the ephemeral storage request can be set to. Used with the KUBERNETES_EPHEMERAL_STORAGE_REQUEST variable in the build. [$KUBERNETES_EPHEMERAL_STORAGE_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-service-cpu-limit value The CPU allocation given to build service containers [$KUBERNETES_SERVICE_CPU_LIMIT] --kubernetes-service-cpu-limit-overwrite-max-allowed value If set, the max amount the service cpu limit can be set to. Used with the KUBERNETES_SERVICE_CPU_LIMIT variable in the build. [$KUBERNETES_SERVICE_CPU_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-service-cpu-request value The CPU allocation requested for build service containers [$KUBERNETES_SERVICE_CPU_REQUEST] --kubernetes-service-cpu-request-overwrite-max-allowed value If set, the max amount the service cpu request can be set to. Used with the KUBERNETES_SERVICE_CPU_REQUEST variable in the build. [$KUBERNETES_SERVICE_CPU_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-service-memory-limit value The amount of memory allocated to build service containers [$KUBERNETES_SERVICE_MEMORY_LIMIT] --kubernetes-service-memory-limit-overwrite-max-allowed value If set, the max amount the service memory limit can be set to. Used with the KUBERNETES_SERVICE_MEMORY_LIMIT variable in the build. [$KUBERNETES_SERVICE_MEMORY_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-service-memory-request value The amount of memory requested for build service containers [$KUBERNETES_SERVICE_MEMORY_REQUEST] --kubernetes-service-memory-request-overwrite-max-allowed value If set, the max amount the service memory request can be set to. Used with the KUBERNETES_SERVICE_MEMORY_REQUEST variable in the build. [$KUBERNETES_SERVICE_MEMORY_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-service-ephemeral_storage-limit value The amount of ephemeral storage allocated to build service containers [$KUBERNETES_SERVICE_EPHEMERAL_STORAGE_LIMIT] --kubernetes-service-ephemeral_storage-limit-overwrite-max-allowed value If set, the max amount the service ephemeral storage limit can be set to. Used with the KUBERNETES_SERVICE_EPHEMERAL_STORAGE_LIMIT variable in the build. [$KUBERNETES_SERVICE_EPHEMERAL_STORAGE_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-service-ephemeral_storage-request value The amount of ephemeral storage requested for build service containers [$KUBERNETES_SERVICE_EPHEMERAL_STORAGE_REQUEST] --kubernetes-service-ephemeral_storage-request-overwrite-max-allowed value If set, the max amount the service ephemeral storage request can be set to. Used with the KUBERNETES_SERVICE_EPHEMERAL_STORAGE_REQUEST variable in the build. [$KUBERNETES_SERVICE_EPHEMERAL_STORAGE_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-helper-cpu-limit value The CPU allocation given to build helper containers [$KUBERNETES_HELPER_CPU_LIMIT] --kubernetes-helper-cpu-limit-overwrite-max-allowed value If set, the max amount the helper cpu limit can be set to. Used with the KUBERNETES_HELPER_CPU_LIMIT variable in the build. [$KUBERNETES_HELPER_CPU_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-helper-cpu-request value The CPU allocation requested for build helper containers [$KUBERNETES_HELPER_CPU_REQUEST] --kubernetes-helper-cpu-request-overwrite-max-allowed value If set, the max amount the helper cpu request can be set to. Used with the KUBERNETES_HELPER_CPU_REQUEST variable in the build. [$KUBERNETES_HELPER_CPU_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-helper-memory-limit value The amount of memory allocated to build helper containers [$KUBERNETES_HELPER_MEMORY_LIMIT] --kubernetes-helper-memory-limit-overwrite-max-allowed value If set, the max amount the helper memory limit can be set to. Used with the KUBERNETES_HELPER_MEMORY_LIMIT variable in the build. [$KUBERNETES_HELPER_MEMORY_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-helper-memory-request value The amount of memory requested for build helper containers [$KUBERNETES_HELPER_MEMORY_REQUEST] --kubernetes-helper-memory-request-overwrite-max-allowed value If set, the max amount the helper memory request can be set to. Used with the KUBERNETES_HELPER_MEMORY_REQUEST variable in the build. [$KUBERNETES_HELPER_MEMORY_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-helper-ephemeral_storage-limit value The amount of ephemeral storage allocated to build helper containers [$KUBERNETES_HELPER_EPHEMERAL_STORAGE_LIMIT] --kubernetes-helper-ephemeral_storage-limit-overwrite-max-allowed value If set, the max amount the helper ephemeral storage limit can be set to. Used with the KUBERNETES_HELPER_EPHEMERAL_STORAGE_LIMIT variable in the build. [$KUBERNETES_HELPER_EPHEMERAL_STORAGE_LIMIT_OVERWRITE_MAX_ALLOWED] --kubernetes-helper-ephemeral_storage-request value The amount of ephemeral storage requested for build helper containers [$KUBERNETES_HELPER_EPHEMERAL_STORAGE_REQUEST] --kubernetes-helper-ephemeral_storage-request-overwrite-max-allowed value If set, the max amount the helper ephemeral storage request can be set to. Used with the KUBERNETES_HELPER_EPHEMERAL_STORAGE_REQUEST variable in the build. [$KUBERNETES_HELPER_EPHEMERAL_STORAGE_REQUEST_OVERWRITE_MAX_ALLOWED] --kubernetes-allowed-images value Image allowlist [$KUBERNETES_ALLOWED_IMAGES] --kubernetes-allowed-services value Service allowlist [$KUBERNETES_ALLOWED_SERVICES] --kubernetes-pull-policy value Policy for if/when to pull a container image (never, if-not-present, always). The cluster default will be used if not set [$KUBERNETES_PULL_POLICY] --kubernetes-node-selector value A toml table/json object of key:value. Value is expected to be a string. When set this will create pods on k8s nodes that match all the key:value pairs. Only one selector is supported through environment variable configuration. (default: "{}") [$KUBERNETES_NODE_SELECTOR] --kubernetes-node-tolerations value A toml table/json object of key=value:effect. Value and effect are expected to be strings. When set, pods will tolerate the given taints. Only one toleration is supported through environment variable configuration. (default: "{}") [$KUBERNETES_NODE_TOLERATIONS] --kubernetes-image-pull-secrets value A list of image pull secrets that are used for pulling docker image [$KUBERNETES_IMAGE_PULL_SECRETS] --kubernetes-helper-image value [ADVANCED] Override the default helper image used to clone repos and upload artifacts [$KUBERNETES_HELPER_IMAGE] --kubernetes-helper-image-flavor value Set helper image flavor (alpine, ubuntu), defaults to alpine [$KUBERNETES_HELPER_IMAGE_FLAVOR] --kubernetes-terminationGracePeriodSeconds value Duration after the processes running in the pod are sent a termination signal and the time when the processes are forcibly halted with a kill signal.DEPRECATED: use KUBERNETES_POD_TERMINATION_GRACE_PERIOD_SECONDS and KUBERNETES_CLEANUP_GRACE_PERIOD_SECONDS instead. [$KUBERNETES_TERMINATIONGRACEPERIODSECONDS] --kubernetes-pod_termination_grace_period_seconds value Pod-level setting which determines the duration in seconds which the pod has to terminate gracefully. After this, the processes are forcibly halted with a kill signal. Ignored if KUBERNETES_TERMINATIONGRACEPERIODSECONDS is specified. [$KUBERNETES_POD_TERMINATION_GRACE_PERIOD_SECONDS] --kubernetes-cleanup_grace_period_seconds value When cleaning up a pod on completion of a job, the duration in seconds which the pod has to terminate gracefully. After this, the processes are forcibly halted with a kill signal. Ignored if KUBERNETES_TERMINATIONGRACEPERIODSECONDS is specified. [$KUBERNETES_CLEANUP_GRACE_PERIOD_SECONDS] --kubernetes-poll-interval value How frequently, in seconds, the runner will poll the Kubernetes pod it has just created to check its status (default: "0") [$KUBERNETES_POLL_INTERVAL] --kubernetes-poll-timeout value The total amount of time, in seconds, that needs to pass before the runner will timeout attempting to connect to the pod it has just created (useful for queueing more builds that the cluster can handle at a time) (default: "0") [$KUBERNETES_POLL_TIMEOUT] --kubernetes-resource-availability-check-max-attempts value The maximum number of attempts to check if a resource (service account and/or pull secret) set is available before giving up. There is 5 seconds interval between each attempt (default: "0") [$KUBERNETES_RESOURCE_AVAILABILITY_CHECK_MAX_ATTEMPTS] --kubernetes-pod-labels value A toml table/json object of key-value. Value is expected to be a string. When set, this will create pods with the given pod labels. Environment variables will be substituted for values here. (default: "{}") --kubernetes-service-account value Executor pods will use this Service Account to talk to kubernetes API [$KUBERNETES_SERVICE_ACCOUNT] --kubernetes-service_account_overwrite_allowed value Regex to validate 'KUBERNETES_SERVICE_ACCOUNT' value [$KUBERNETES_SERVICE_ACCOUNT_OVERWRITE_ALLOWED] --kubernetes-pod-annotations value A toml table/json object of key-value. Value is expected to be a string. When set, this will create pods with the given annotations. Can be overwritten in build with KUBERNETES_POD_ANNOTATION_* variables (default: "{}") --kubernetes-pod_annotations_overwrite_allowed value Regex to validate 'KUBERNETES_POD_ANNOTATIONS_*' values [$KUBERNETES_POD_ANNOTATIONS_OVERWRITE_ALLOWED] --kubernetes-pod-security-context-fs-group value A special supplemental group that applies to all containers in a pod [$KUBERNETES_POD_SECURITY_CONTEXT_FS_GROUP] --kubernetes-pod-security-context-run-as-group value The GID to run the entrypoint of the container process [$KUBERNETES_POD_SECURITY_CONTEXT_RUN_AS_GROUP] --kubernetes-pod-security-context-run-as-non-root value Indicates that the container must run as a non-root user [$KUBERNETES_POD_SECURITY_CONTEXT_RUN_AS_NON_ROOT] --kubernetes-pod-security-context-run-as-user value The UID to run the entrypoint of the container process [$KUBERNETES_POD_SECURITY_CONTEXT_RUN_AS_USER] --kubernetes-pod-security-context-supplemental-groups value A list of groups applied to the first process run in each container, in addition to the container's primary GID --kubernetes-build_container_security_context-capabilities-add value List of capabilities to add to the build container [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_CAPABILITIES_ADD] --kubernetes-build_container_security_context-capabilities-drop value List of capabilities to drop from the build container [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_CAPABILITIES_DROP] --kubernetes-build_container_security_context-privileged value Run container in privileged mode [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_PRIVILEGED] --kubernetes-build_container_security_context-run-as-user value The UID to run the entrypoint of the container process [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_RUN_AS_USER] --kubernetes-build_container_security_context-run-as-group value The GID to run the entrypoint of the container process [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_RUN_AS_GROUP] --kubernetes-build_container_security_context-run-as-non-root value Indicates that the container must run as a non-root user [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_RUN_AS_NON_ROOT] --kubernetes-build_container_security_context-read-only-root-filesystem value Whether this container has a read-only root filesystem. [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_READ_ONLY_ROOT_FILESYSTEM] --kubernetes-build_container_security_context-allow-privilege-escalation value AllowPrivilegeEscalation controls whether a process can gain more privileges than its parent process [$KUBERNETES_BUILD_CONTAINER_SECURITY_CONTEXT_ALLOW_PRIVILEGE_ESCALATION] --kubernetes-helper_container_security_context-capabilities-add value List of capabilities to add to the build container [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_CAPABILITIES_ADD] --kubernetes-helper_container_security_context-capabilities-drop value List of capabilities to drop from the build container [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_CAPABILITIES_DROP] --kubernetes-helper_container_security_context-privileged value Run container in privileged mode [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_PRIVILEGED] --kubernetes-helper_container_security_context-run-as-user value The UID to run the entrypoint of the container process [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_RUN_AS_USER] --kubernetes-helper_container_security_context-run-as-group value The GID to run the entrypoint of the container process [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_RUN_AS_GROUP] --kubernetes-helper_container_security_context-run-as-non-root value Indicates that the container must run as a non-root user [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_RUN_AS_NON_ROOT] --kubernetes-helper_container_security_context-read-only-root-filesystem value Whether this container has a read-only root filesystem. [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_READ_ONLY_ROOT_FILESYSTEM] --kubernetes-helper_container_security_context-allow-privilege-escalation value AllowPrivilegeEscalation controls whether a process can gain more privileges than its parent process [$KUBERNETES_HELPER_CONTAINER_SECURITY_CONTEXT_ALLOW_PRIVILEGE_ESCALATION] --kubernetes-service_container_security_context-capabilities-add value List of capabilities to add to the build container [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_CAPABILITIES_ADD] --kubernetes-service_container_security_context-capabilities-drop value List of capabilities to drop from the build container [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_CAPABILITIES_DROP] --kubernetes-service_container_security_context-privileged value Run container in privileged mode [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_PRIVILEGED] --kubernetes-service_container_security_context-run-as-user value The UID to run the entrypoint of the container process [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_RUN_AS_USER] --kubernetes-service_container_security_context-run-as-group value The GID to run the entrypoint of the container process [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_RUN_AS_GROUP] --kubernetes-service_container_security_context-run-as-non-root value Indicates that the container must run as a non-root user [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_RUN_AS_NON_ROOT] --kubernetes-service_container_security_context-read-only-root-filesystem value Whether this container has a read-only root filesystem. [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_READ_ONLY_ROOT_FILESYSTEM] --kubernetes-service_container_security_context-allow-privilege-escalation value AllowPrivilegeEscalation controls whether a process can gain more privileges than its parent process [$KUBERNETES_SERVICE_CONTAINER_SECURITY_CONTEXT_ALLOW_PRIVILEGE_ESCALATION] --kubernetes-host_aliases value Add a custom host-to-IP mapping --kubernetes-cap-add value Add Linux capabilities [$KUBERNETES_CAP_ADD] --kubernetes-cap-drop value Drop Linux capabilities [$KUBERNETES_CAP_DROP] --kubernetes-dns-policy value How Kubernetes should try to resolve DNS from the created pods. If unset, Kubernetes will use the default 'ClusterFirst'. Valid values are: none, default, cluster-first, cluster-first-with-host-net [$KUBERNETES_DNS_POLICY] --custom-config-exec value Executable that allows to inject configuration values to the executor [$CUSTOM_CONFIG_EXEC] --custom-config-args value Arguments for the config executable --custom-config-exec-timeout value Timeout for the config executable (in seconds) [$CUSTOM_CONFIG_EXEC_TIMEOUT] --custom-prepare-exec value Executable that prepares executor [$CUSTOM_PREPARE_EXEC] --custom-prepare-args value Arguments for the prepare executable --custom-prepare-exec-timeout value Timeout for the prepare executable (in seconds) [$CUSTOM_PREPARE_EXEC_TIMEOUT] --custom-run-exec value Executable that runs the job script in executor [$CUSTOM_RUN_EXEC] --custom-run-args value Arguments for the run executable --custom-cleanup-exec value Executable that cleanups after executor run [$CUSTOM_CLEANUP_EXEC] --custom-cleanup-args value Arguments for the cleanup executable --custom-cleanup-exec-timeout value Timeout for the cleanup executable (in seconds) [$CUSTOM_CLEANUP_EXEC_TIMEOUT] --custom-graceful-kill-timeout value Graceful timeout for scripts execution after SIGTERM is sent to the process (in seconds). This limits the time given for scripts to perform the cleanup before exiting [$CUSTOM_GRACEFUL_KILL_TIMEOUT] --custom-force-kill-timeout value Force timeout for scripts execution (in seconds). Counted from the force kill call; if process will be not terminated, Runner will abandon process termination and log an error [$CUSTOM_FORCE_KILL_TIMEOUT] |
- 本文固定链接: https://www.yoyoask.com/?p=4498
- 转载请注明: shooter 于 SHOOTER 发表