ISCSI 带身份验证登录
一、单向认证(CHAP)
开启并配置CHAP(配置单向普通session认证,discover认证。修改下面的内容:)
|
1 |
vim /etc/iscsi/iscsid.conf |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
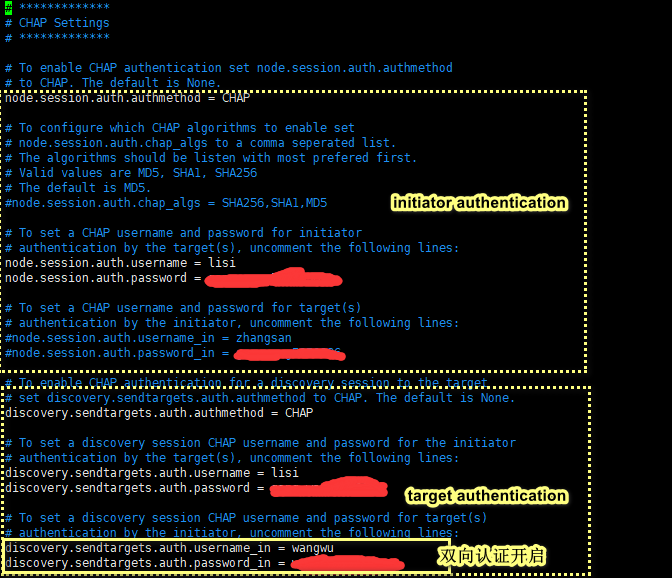
# To enable CHAP authentication set node.session.auth.authmethod # to CHAP. The default is None. node.session.auth.authmethod = CHAP # To configure which CHAP algorithms to enable set # node.session.auth.chap_algs to a comma seperated list. # The algorithms should be listen with most prefered first. # Valid values are MD5, SHA1, SHA256 # The default is MD5. #node.session.auth.chap_algs = SHA256,SHA1,MD5 # To set a CHAP username and password for initiator # authentication by the target(s), uncomment the following lines: node.session.auth.username = shooter node.session.auth.password = 123456 # To set a CHAP username and password for target(s) # authentication by the initiator, uncomment the following lines: #node.session.auth.username_in = shooter #node.session.auth.password_in = 123456 # To enable CHAP authentication for a discovery session to the target # set discovery.sendtargets.auth.authmethod to CHAP. The default is None. discovery.sendtargets.auth.authmethod = CHAP # To set a discovery session CHAP username and password for the initiator # authentication by the target(s), uncomment the following lines: discovery.sendtargets.auth.username = shooter discovery.sendtargets.auth.password = 123456 # To set a discovery session CHAP username and password for target(s) # authentication by the initiator, uncomment the following lines: #discovery.sendtargets.auth.username_in = shooter #discovery.sendtargets.auth.password_in = 123456 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
#解释 initiator authentication认证: 在initiator尝试连接到一个target的时候,initator需要提供一个用户名和密码给target被target进行认证。 也就是说initiator需要被target认证,它向target端提供的账号和密码是target端指定的。 这个账号和密码对于target来说是流入的账号和密码,用incoming表示。 称呼这个账号和密码为:incoming账号和incoming密码。 即,incoming账号是initiator端提供给target端,被target端认证的账号。 target authentication认证: 在initiator尝试连接到一个target的时候,target有时也需要被initiator认证,以确保该target是合法而非伪装的target,这就要求target提供一个用户名和密码给initiator被initiator进行认证。 target向initiator提供的账号和密码对于target而言是流出的,所以称之为outgoing。 称呼这个账号和密码为:outgoing账号和outgoing密码。 而对于initiator而言是incoming的,所以在initiator配置文件中称为in。 也就是说outgoing账号是target端提供给initiator端,被initiator认证的账号,但尽管如此,这个账号和密码还是在target端创建和绑定的。 单/双向认证: 两种认证方式是有层次顺序的。 一般来说,有认证需求的时候都是服务器验证客户端是否有权限,iscsi也一样。 initiator authentication可以单独存在,它可以在没有target authentication的情况下应用,这时候的CHAP认证就是单向认证(target认证initiator的合法性)。 但target authentication只有在initiator authentication的基础上才能进行。也就是说target认证和initiator认证必须同时存在才可以。即initiator和target需要相互认证实现双向CHAP认证。 注意:发现认证和登录认证都支持单/双向认证。 |
客户端修改配置完成后,一定要在客户端上重新discovery一次target,不然修改的信息是不会生效的
|
1 2 |
systemctl restart iscsid #配置完成后重启下 iscsiadm -m discovery -t sendtargets -p 192.168.66.120:3267 |
|
1 2 3 4 5 6 |
iscsiadm --mode node --targetname iqn.2005-10.org.freenas.ctl:iscsi-shooter --portal 192.168.66.120:3267 --login [root@freeipa ~]# iscsiadm --mode node --targetname iqn.2005-10.org.freenas.ctl:iscsi-shooter --portal 192.168.66.120:3267 --login Logging in to [iface: default, target: iqn.2005-10.org.freenas.ctl:iscsi-shooter, portal: 192.168.66.120,3267] (multiple) Login to [iface: default, target: iqn.2005-10.org.freenas.ctl:iscsi-shooter, portal: 192.168.66.120,3267] successful. |
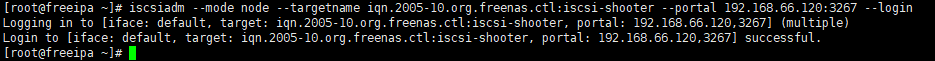
查看块设备
|
1 |
lsblk |
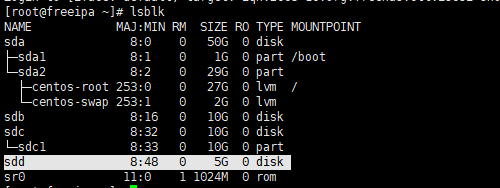
二、双向认证(CHAP)
1、添加一个用户,作为双向认证用户
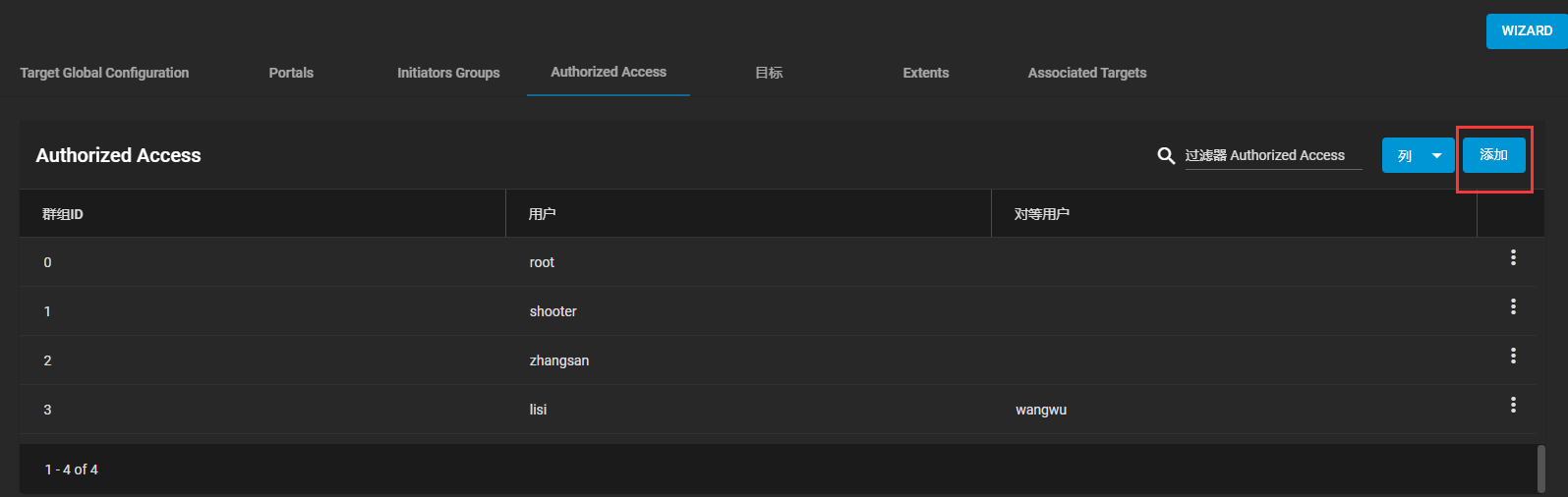
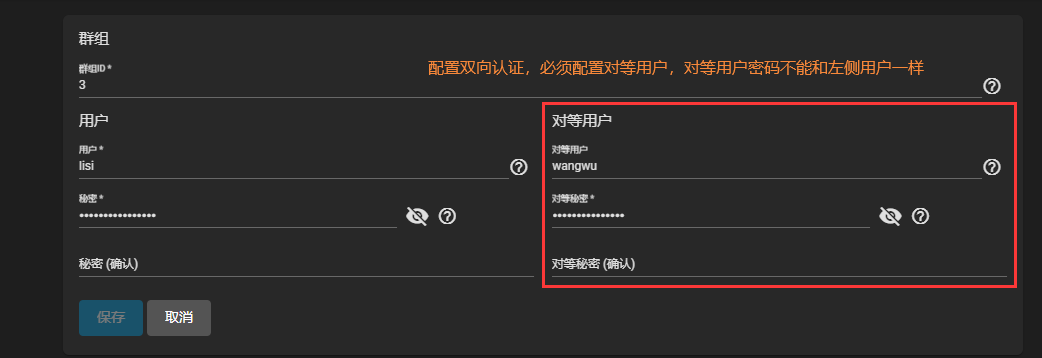
2、设置target接口为双向认证
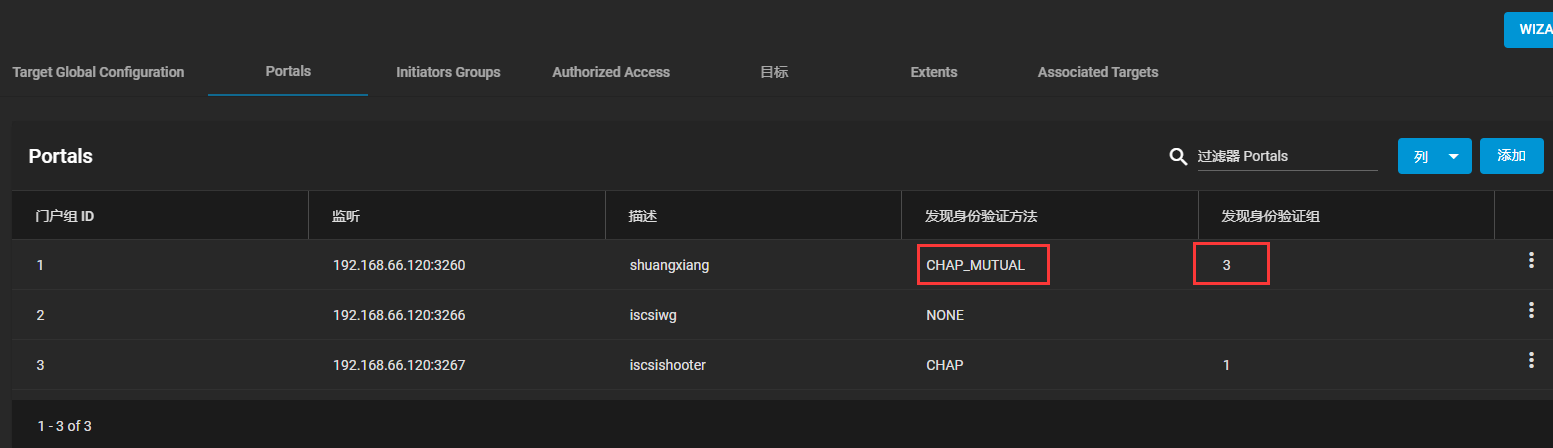
3.配置客户端配置文件
|
1 |
vim /etc/iscsi/iscsid.conf |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
# ************* # CHAP Settings # ************* # To enable CHAP authentication set node.session.auth.authmethod # to CHAP. The default is None. node.session.auth.authmethod = CHAP # To configure which CHAP algorithms to enable set # node.session.auth.chap_algs to a comma seperated list. # The algorithms should be listen with most prefered first. # Valid values are MD5, SHA1, SHA256 # The default is MD5. #node.session.auth.chap_algs = SHA256,SHA1,MD5 # To set a CHAP username and password for initiator # authentication by the target(s), uncomment the following lines: node.session.auth.username = lisi node.session.auth.password = 654321 # To set a CHAP username and password for target(s) # authentication by the initiator, uncomment the following lines: #node.session.auth.username_in = zhangsan #node.session.auth.password_in = 654321 # To enable CHAP authentication for a discovery session to the target # set discovery.sendtargets.auth.authmethod to CHAP. The default is None. discovery.sendtargets.auth.authmethod = CHAP # To set a discovery session CHAP username and password for the initiator # authentication by the target(s), uncomment the following lines: discovery.sendtargets.auth.username = lisi discovery.sendtargets.auth.password = 654321 # To set a discovery session CHAP username and password for target(s) # authentication by the initiator, uncomment the following lines: discovery.sendtargets.auth.username_in = wangwu discovery.sendtargets.auth.password_in = 123456 |
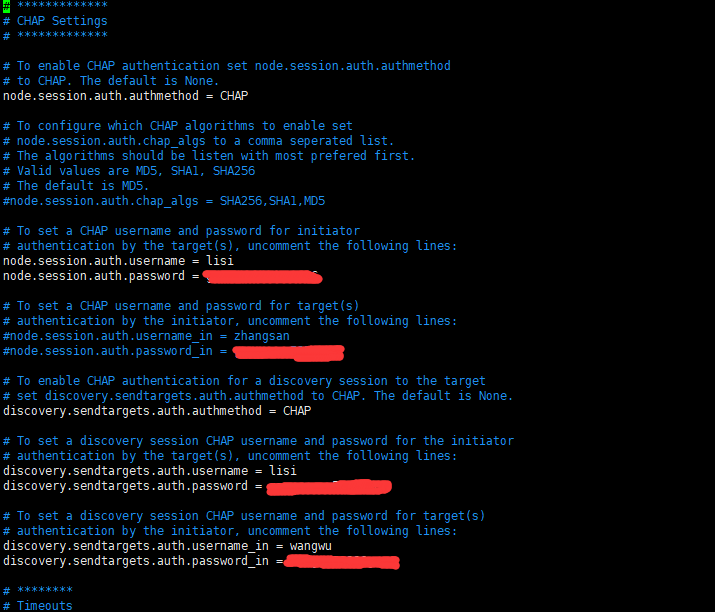
4、重启连接
|
1 2 3 4 |
systemctl restart iscsid iscsiadm -m discovery -t sendtargets -p 192.168.66.120 #登录 iscsiadm --mode node --targetname iqn.2005-10.org.freenas.ctl:vol-iso --portal 192.168.66.120 --login |
|
1 2 3 4 5 6 |
[root@freeipa ~]# iscsiadm -m discovery -t sendtargets -p 192.168.66.120 192.168.66.120:3260,1 iqn.2005-10.org.freenas.ctl:vol-iso [root@freeipa ~]# iscsiadm --mode node --targetname iqn.2005-10.org.freenas.ctl:vol-iso --portal 192.168.66.120 --login Logging in to [iface: default, target: iqn.2005-10.org.freenas.ctl:vol-iso, portal: 192.168.66.120,3260] (multiple) Login to [iface: default, target: iqn.2005-10.org.freenas.ctl:vol-iso, portal: 192.168.66.120,3260] successful. [root@freeipa ~]# |
- 本文固定链接: https://www.yoyoask.com/?p=10655
- 转载请注明: shooter 于 SHOOTER 发表